CHSH inequality
In physics, the CHSH inequality can be used in the proof of Bell's theorem, which states that certain consequences of entanglement in quantum mechanics cannot be reproduced by local hidden-variable theories. Experimental verification of the inequality being violated is seen as confirmation that nature cannot be described by such theories. CHSH stands for John Clauser, Michael Horne, Abner Shimony, and Richard Holt, who described it in a much-cited paper published in 1969.[1] They derived the CHSH inequality, which, as with John Stewart Bell's original inequality,[2] is a constraint on the statistical occurrence of "coincidences" in a Bell test which is necessarily true if there exist underlying local hidden variables, an assumption that is sometimes termed local realism. In practice, the inequality is routinely violated by modern experiments in quantum mechanics.[3]
Statement
The usual form of the CHSH inequality is
|
(1) |
where
|
(2) |
a and a′ are detector settings on side A, b and b′ on side B, the four combinations being tested in separate subexperiments. The terms E(a, b) etc. are the quantum correlations of the particle pairs, where the quantum correlation is defined to be the expectation value of the product of the "outcomes" of the experiment, i.e. the statistical average of A(a)·B(b), where A and B are the separate outcomes, using the coding +1 for the '+' channel and −1 for the '−' channel. Clauser et al.'s 1969[1] derivation was oriented towards the use of "two-channel" detectors, and indeed it is for these that it is generally used, but under their method the only possible outcomes were +1 and −1. In order to adapt to real situations, which at the time meant the use of polarised light and single-channel polarisers, they had to interpret '−' as meaning "non-detection in the '+' channel", i.e. either '−' or nothing. They did not in the original article discuss how the two-channel inequality could be applied in real experiments with real imperfect detectors, though it was later proved[4] that the inequality itself was equally valid. The occurrence of zero outcomes, though, means it is no longer so obvious how the values of E are to be estimated from the experimental data.
The mathematical formalism of quantum mechanics predicts a maximum value for S of 2√2 (Tsirelson's bound),[5] which is greater than 2, and CHSH violations are therefore predicted by the theory of quantum mechanics.
Experiments
Many Bell tests conducted subsequent to Alain Aspect's second experiment in 1982 have used the CHSH inequality, estimating the terms using (3) and assuming fair sampling. Some dramatic violations of the inequality have been reported.[6]
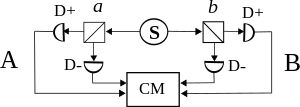
The source S produces pairs of photons, sent in opposite directions. Each photon encounters a two-channel polariser whose orientation can be set by the experimenter. Emerging signals from each channel are detected and coincidences counted by the coincidence monitor CM.
In practice most actual experiments have used light rather than the electrons that Bell originally had in mind. The property of interest is, in the best known experiments,[7][8][9] the polarisation direction, though other properties can be used. The diagram shows a typical optical experiment. Coincidences (simultaneous detections) are recorded, the results being categorised as '++', '+−', '−+' or '−−' and corresponding counts accumulated.
Four separate subexperiments are conducted, corresponding to the four terms in the test statistic S (2, above). The settings a = 0°, a′ = 45°, b = 22.5°, and b′ = 67.5° are generally in practice chosen — the "Bell test angles" — these being the ones for which the quantum mechanical formula gives the greatest violation of the inequality.
For each selected value of a and b, the numbers of coincidences in each category are recorded. The experimental estimate for is then calculated as:
|
(3) |
Once all the E's have been estimated, an experimental estimate of S (Eq. 2) can be found. If it is numerically greater than 2 it has infringed the CHSH inequality and the experiment is declared to have supported the quantum mechanics prediction and ruled out all local hidden-variable theories.
The CHSH paper lists many preconditions (or "reasonable and/or presumable assumptions") to derive the simplified theorem and formula. For example, for the method to be valid, it has to be assumed that the detected pairs are a fair sample of those emitted. In actual experiments, detectors are never 100% efficient, so that only a sample of the emitted pairs are detected. A subtle, related requirement is that the hidden variables do not influence or determine detection probability in a way that would lead to different samples at each arm of the experiment.
Various labs have been entangled and violated the CHSH inequality with photon pairs, beryllium ion pairs, ytterbium ion pairs, rubidium atom pairs, whole rubidium-atom cloud pairs, nitrogen vacancies in diamonds, and Josephson phase qubits.[10]
Derivation
The original 1969 derivation will not be given here since it is not easy to follow and involves the assumption that the outcomes are all +1 or −1, never zero. Bell's 1971 derivation is more general. He effectively assumes the "Objective Local Theory" later used by Clauser and Horne.[11] It is assumed that any hidden variables associated with the detectors themselves are independent on the two sides and can be averaged out from the start. Another derivation of interest is given in Clauser and Horne's 1974 paper, in which they start from the CH74 inequality.
It would appear from both these later derivations that the only assumptions really needed for the inequality itself (as opposed to the method of estimation of the test statistic) are that the distribution of the possible states of the source remains constant and the detectors on the two sides act independently.
Bell's 1971 derivation
The following is based on page 37 of Bell's Speakable and Unspeakable,[4] the main change being to use the symbol ‘E’ instead of ‘P’ for the expected value of the quantum correlation. This avoids any suggestion that the quantum correlation is itself a probability.
We start with the standard assumption of independence of the two sides, enabling us to obtain the joint probabilities of pairs of outcomes by multiplying the separate probabilities, for any selected value of the "hidden variable" λ. λ is assumed to be drawn from a fixed distribution of possible states of the source, the probability of the source being in the state λ for any particular trial being given by the density function ρ(λ), the integral of which over the complete hidden variable space is 1. We thus assume we can write:
where A and B are the outcomes. Since the possible values of A and B are −1, 0 and +1, it follows that:
-
(4)
Then, if a, a′, b and b′ are alternative settings for the detectors,
Taking absolute values of both sides, and applying the triangle inequality to the right-hand side, we obtain
We use the fact that and are both non-negative to rewrite the right-hand side of this as
By (4), this must be less than or equal to
which, using the fact that the integral of ρ(λ) is 1, is equal to
which is equal to .
Putting this together with the left-hand side, we have:
which means that the left-hand side is less than or equal to both and . That is:
from which we obtain
(by the triangle inequality again), which is the CHSH inequality.
Derivation from Clauser and Horne's 1974 inequality
In their 1974 paper,[11] Clauser and Horne show that the CHSH inequality can be derived from the CH74 one. As they tell us, in a two-channel experiment the CH74 single-channel test is still applicable and provides four sets of inequalities governing the probabilities p of coincidences.
Working from the inhomogeneous version of the inequality, we can write:
where j and k are each '+' or '−', indicating which detectors are being considered.
To obtain the CHSH test statistic S (2), all that is needed is to multiply the inequalities for which j is different from k by −1 and add these to the inequalities for which j and k are the same.
Optimal violation by a general quantum state
In experimental practice, the two particles are not an ideal EPR pair. There is a necessary and sufficient condition for a two-qubit density matrix to violate the CHSH inequality, expressed by the maximum attainable polynomial Smax defined in Eq. 2.[12] This is important in entanglement-based quantum key distribution, where the secret key rate depends on the degree of measurement correlations.[13]
Let us introduce a 3×3 real matrix with elements , where are the Pauli matrices. Then we find the eigensystem of the real symmetric matrix ,
where the indices are sorted by . Then, the maximal CHSH polynomial is determined by the two greatest eigenvalues,[12]
Optimal measurement bases
There exists an optimal configuration of the measurement bases a, a', b, b' for a given that yields Smax with at least one free parameter.[14][15]
The projective measurement that yields either +1 or −1 for two orthogonal states respectively, can be expressed by an operator . The choice of this measurement basis can be parametrized by a real unit vector and the Pauli vector by expressing . Then, the expected correlation in bases a, b is
The numerical values of the basis vectors, when found, can be directly translated to the configuration of the projective measurements.[15]
The optimal set of bases for the state is found by taking the two greatest eigenvalues and the corresponding eigenvectors of , and finding the auxiliary unit vectors
where is a free parameter. We also calculate the acute angle
to obtain the bases that maximize Eq. 2,
In entanglement-based quantum key distribution, there is another measurement basis used to communicate the secret key ( assuming Alice uses the side A). The bases then need to minimize the quantum bit error rate Q, which is the probability of obtaining different measurement outcomes (+1 on one particle and −1 on the other).[13] The corresponding bases are[15]
The CHSH polynomial S needs to be maximized as well, which together with the bases above creates the constraint .[15]
CHSH game
The CHSH game is a thought experiment involving two parties separated at a great distance (far enough to preclude classical communication at the speed of light), each of whom has access to one half of an entangled two-qubit pair. Analysis of this game shows that no classical local hidden-variable theory can explain the correlations that can result from entanglement. Since this game is indeed physically realizable, this gives strong evidence that classical physics is fundamentally incapable of explaining certain quantum phenomena, at least in a "local" fashion.
In the CHSH game, there are two cooperating players, Alice and Bob, and a referee, Charlie. These agents will be abbreviated respectively. At the start of the game, Charlie chooses bits uniformly at random, and then sends to Alice and to Bob. Alice and Bob must then each respond to Charlie with bits respectively. Now, once Alice and Bob send their responses back to Charlie, Charlie tests if . If this equality holds, then Alice and Bob win, and if not then they lose.
It is also required that Alice and Bob's responses can only depend on the bits they see: so Alice's response depends only on , and similarly for Bob. This means that Alice and Bob are forbidden from directly communicating with each other about the values of the bits sent to them by Charlie. However, Alice and Bob are allowed to decide on a common strategy before the game begins.
In the following sections, it is shown that if Alice and Bob use only classical strategies involving their local information (and potentially some random coin tosses), it is impossible for them to win with a probability higher than 75%. However, if Alice and Bob are allowed to share a single entangled qubit pair, then there exists a strategy which allows Alice and Bob to succeed with a probability of ~85%.
Optimal classical strategy
We first establish that any deterministic classical strategy has success probability at most 75% (where the probability is taken over Charlie's uniformly random choice of ). By a deterministic strategy, we mean a pair of functions , where is a function determining Alice's response as a function of the message she receives from Charlie, and is a function determining Bob's response based on what he receives. To prove that any deterministic strategy fails at least 25% of the time, we can simply consider all possible pairs of strategies for Alice and Bob, of which there are at most 8 (for each party, there are 4 functions ). It can be verified that for each of those 8 strategies there is always at least one out of the four possible input pairs which makes the strategy fail. For example, in the strategy where both players always answer 0, we have that Alice and Bob win in all cases except for when , so using this strategy their win probability is exactly 75%.
Now, consider the case of randomized classical strategies, where Alice and Bob have access to correlated random numbers. They can be produced by jointly flipping a coin several times before the game has started and Alice and Bob are still allowed to communicate. The output they give at each round is then a function of both Charlie's message and the outcome of the corresponding coin flip. Such a strategy can be viewed as a probability distribution over deterministic strategies, and thus its success probability is a weighted sum over the success probabilities of the deterministic strategies. But since every deterministic strategy has a success probability of at most 75%, this weighted sum cannot exceed 75% either.
Optimal quantum strategy
Now, imagine that Alice and Bob share the two-qubit entangled state: , commonly referred to as an EPR pair. Alice and Bob will use this entangled pair in their strategy as described below. The optimality of this strategy then follows from Tsirelson's bound.
Upon receiving the bit from Charlie, Alice will measure her qubit in the basis or in the basis , conditionally on whether or , respectively. She will then label the two possible outputs resulting from each measurement choice as if the first state in the measurement basis is observed, and otherwise.
Bob also uses the bit received from Charlie to decide which measurement to perform: if he measures in the basis , while if he measures in the basis , where
with .
To analyze the success probability, it suffices to analyze the probability that they output a winning value pair on each of the four possible inputs , and then take the average. We analyze the case where here: In this case the winning response pairs are and . On input , we know that Alice will measure in the basis , and Bob will measure in the basis . Then the probability that they both output 0 is the same as the probability that their measurements yield respectively, so precisely . Similarly, the probability that they both output 1 is exactly . So the probability that either of these successful outcomes happens is .
In the case of the 3 other possible input pairs, essentially identical analysis shows that Alice and Bob will have the same win probability of , so overall the average win probability for a randomly chosen input is . Since , this is strictly better than what was possible in the classical case.
Modeling general quantum strategies
An arbitrary quantum strategy for the CHSH game can be modeled as a triple where
- is a bipartite state for some ,
- and are Alice's observables each corresponding to receiving from the referee, and
- and are Bob's observables each corresponding to receiving from the referee.
The optimal quantum strategy described above can be recast in this notation as follows: is the EPR pair , the observable (corresponding to Alice measuring in the basis), the observable (corresponding to Alice measuring in the basis), where and are Pauli matrices. The observables and (corresponding to each of Bob's choice of basis to measure in). We will denote the success probability of a strategy in the CHSH game by , and we define the bias of the strategy as , which is the difference between the winning and losing probabilities of .
In particular, we have
The bias of the quantum strategy described above is .
Tsirelson's inequality and CHSH rigidity
Tsirelson's inequality, discovered by Boris Tsirelson in 1980,[16] states that for any quantum strategy for the CHSH game, the bias . Equivalently, it states that success probability
for any quantum strategy for the CHSH game. In particular, this implies the optimality of the quantum strategy described above for the CHSH game.
Tsirelsen's inequality establishes that the maximum success probability of any quantum strategy is , and we saw that this maximum success probability is achieved by the quantum strategy described above. In fact, any quantum strategy that achieves this maximum success probability must be isomorphic (in a precise sense) to the canonical quantum strategy described above; this property is called the rigidity of the CHSH game, first attributed to Summers and Werner.[17] More formally, we have the following result:
Theorem (Exact CHSH rigidity) — Let be a quantum strategy for the CHSH game where such that . Then there exist isometries and where are isomorphic to such that letting we have
where denotes the EPR pair and denotes some pure state, and
Informally, the above theorem states that given an arbitrary optimal strategy for the CHSH game, there exists a local change-of-basis (given by the isometries ) for Alice and Bob such that their shared state factors into the tensor of an EPR pair and an additional auxiliary state . Furthermore, Alice and Bob's observables and behave, up to unitary transformations, like the and observables on their respective qubits from the EPR pair. An approximate or quantitative version of CHSH rigidity was obtained by McKague, et al.[18] who proved that if you have a quantum strategy such that for some , then there exist isometries under which the strategy is -close to the canonical quantum strategy. Representation-theoretic proofs of approximate rigidity are also known.[19]
Applications
Note that the CHSH game can be viewed as a test for quantum entanglement and quantum measurements, and that the rigidity of the CHSH game lets us test for a specific entanglement as well as specific quantum measurements. This in turn can be leveraged to test or even verify entire quantum computations—in particular, the rigidity of CHSH games has been harnessed to construct protocols for verifiable quantum delegation,[20][21] certifiable randomness expansion,[22] and device-independent cryptography.[23]
References
- J.F. Clauser; M.A. Horne; A. Shimony; R.A. Holt (1969), "Proposed experiment to test local hidden-variable theories", Phys. Rev. Lett., 23 (15): 880–4, Bibcode:1969PhRvL..23..880C, doi:10.1103/PhysRevLett.23.880
- J.S. Bell (1964), "On the Einstein Podolsky Rosen Paradox", Physics Physique Физика, 1 (3): 195–200, doi:10.1103/PhysicsPhysiqueFizika.1.195, reproduced as Ch. 2 of J. S. Bell (1987), Speakable and Unspeakable in Quantum Mechanics, Cambridge University Press
- Markoff, Jack (21 October 2015). "Sorry, Einstein. Quantum Study Suggests 'Spooky Action' Is Real". New York Times. Retrieved 21 October 2015.
- J. S. Bell, in Foundations of Quantum Mechanics, Proceedings of the International School of Physics “Enrico Fermi”, Course XLIX, B. d’Espagnat (Ed.) (Academic, New York, 1971), p. 171 and Appendix B. Pages 171-81 are reproduced as Ch. 4 of J. S. Bell, Speakable and Unspeakable in Quantum Mechanics (Cambridge University Press 1987)
- Cirel'son, B. S. (March 1980). "Quantum generalizations of Bell's inequality". Letters in Mathematical Physics. 4 (2): 93–100. Bibcode:1980LMaPh...4...93C. doi:10.1007/BF00417500. S2CID 120680226.
- Hensen, B.; Bernien, H.; Dréau, A. E.; Reiserer, A.; Kalb, N.; Blok, M. S.; Ruitenberg, J.; Vermeulen, R. F. L.; Schouten, R. N.; Abellán, C.; Amaya, W.; Pruneri, V.; Mitchell, M. W.; Markham, M.; Twitchen, D. J.; Elkouss, D.; Wehner, S.; Taminiau, T. H.; Hanson, R. (2015). "Loophole-free Bell inequality violation using electron spins separated by 1.3 kilometres". Nature. 526 (7575): 682–686. arXiv:1508.05949. Bibcode:2015Natur.526..682H. doi:10.1038/nature15759. PMID 26503041. S2CID 205246446.
- Alain Aspect; Philippe Grangier; Gérard Roger (1981), "Experimental Tests of Realistic Local Theories via Bell's Theorem", Phys. Rev. Lett., 47 (7): 460–3, Bibcode:1981PhRvL..47..460A, doi:10.1103/PhysRevLett.47.460
- Alain Aspect; Philippe Grangier; Gérard Roger (1982), "Experimental Realization of Einstein-Podolsky-Rosen-Bohm Gedankenexperiment: A New Violation of Bell's Inequalities", Phys. Rev. Lett., 49 (2): 91, Bibcode:1982PhRvL..49...91A, doi:10.1103/PhysRevLett.49.91
- Alain Aspect; Jean Dalibard; Gérard Roger (1982), "Experimental Test of Bell's Inequalities Using Time-Varying Analyzers", Phys. Rev. Lett., 49 (25): 1804–7, Bibcode:1982PhRvL..49.1804A, doi:10.1103/PhysRevLett.49.1804
- "First Experimental Proof That Quantum Entanglement Is Real". SciTech Daily. 9 October 2022. Retrieved October 10, 2022.
- J.F. Clauser; M.A. Horne (1974), "Experimental consequences of objective local theories", Phys. Rev. D, 10 (2): 526–35, Bibcode:1974PhRvD..10..526C, doi:10.1103/PhysRevD.10.526
- R. Horodecki; P. Horodecki; M. Horodecki (1995), "Violating Bell inequality by mixed spin- states: Necessary and sufficient condition", Phys.Lett. A, 200 (5): 340–344, doi:10.1016/0375-9601(95)00214-N
- Stefano Pironio; Antonio Acín; Nicolas Brunner; Nicolas Gisin; Serge Massar; Valerio Scarani (2009), "Device-independent quantum key distribution secure against collective attacks", New J. Phys., 11 (4): 045021, arXiv:0903.4460, Bibcode:2009NJPh...11d5021P, doi:10.1088/1367-2630/11/4/045021, S2CID 7971771
- A. G. Kofman (2012), "Optimal conditions for Bell-inequality violation in the presence of decoherence and errors", Quantum Inf. Process., 11: 269–309, arXiv:0804.4167, doi:10.1007/s11128-011-0242-1, S2CID 41329613
- R. Hošák; I. Straka; A. Predojević; R. Filip; M. Ježek (2021), "Effect of source statistics on utilizing photon entanglement in quantum key distribution", Phys. Rev. A, 103 (4): 042411, arXiv:2008.07501, Bibcode:2021PhRvA.103d2411H, doi:10.1103/PhysRevA.103.042411, S2CID 221140079
- "Quantum generalizations of Bell's inequality". www.tau.ac.il.
- Maximal violation of Bell's inequalities is generic in quantum field theory, Summers and Werner (1987)
- McKague, M; Yang, T H; Scarani, V (October 19, 2012). "Robust self-testing of the singlet". Journal of Physics A: Mathematical and Theoretical. 45 (45): 455304. arXiv:1203.2976. doi:10.1088/1751-8113/45/45/455304. S2CID 118535156.
- "UCSD Summer School Notes: Quantum multiplayer games, testing and rigidity, Thomas Vidick (2018)" (PDF).
- Coladangelo, Andrea; Grilo, Alex; Jeffery, Stacey; Vidick, Thomas (January 9, 2020). "Verifier-on-a-Leash: new schemes for verifiable delegated quantum computation, with quasilinear resources". arXiv:1708.07359 [quant-ph].
- Grilo, Alex B. (June 5, 2020). "A simple protocol for verifiable delegation of quantum computation in one round". arXiv:1711.09585 [quant-ph].
- Vazirani, Umesh V.; Vidick, Thomas (November 25, 2011). "Certifiable Quantum Dice - Or, testable exponential randomness expansion". arXiv:1111.6054 [quant-ph].
- Vazirani, Umesh; Vidick, Thomas (September 29, 2014). "Fully device independent quantum key distribution". Physical Review Letters. 113 (14): 140501. arXiv:1210.1810. Bibcode:2014PhRvL.113n0501V. doi:10.1103/PhysRevLett.113.140501. PMID 25325625. S2CID 119299119.