Executable and Linkable Format
In computing, the Executable and Linkable Format[2] (ELF, formerly named Extensible Linking Format), is a common standard file format for executable files, object code, shared libraries, and core dumps. First published in the specification for the application binary interface (ABI) of the Unix operating system version named System V Release 4 (SVR4),[3] and later in the Tool Interface Standard,[1] it was quickly accepted among different vendors of Unix systems. In 1999, it was chosen as the standard binary file format for Unix and Unix-like systems on x86 processors by the 86open project.
| Filename extension |
none, .axf, .bin, .elf, .o, .out, .prx, .puff, .ko, .mod, and .so |
|---|---|
| Magic number | 0x7F 'E' 'L' 'F' |
| Developed by | Unix System Laboratories[1]: 3 |
| Type of format | Binary, executable, object, shared library, core dump |
| Container for | Many executable binary formats |
By design, the ELF format is flexible, extensible, and cross-platform. For instance, it supports different endiannesses and address sizes so it does not exclude any particular central processing unit (CPU) or instruction set architecture. This has allowed it to be adopted by many different operating systems on many different hardware platforms.
File layout
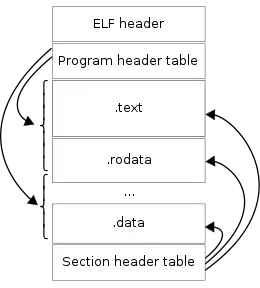
Each ELF file is made up of one ELF header, followed by file data. The data can include:
- Program header table, describing zero or more memory segments
- Section header table, describing zero or more sections
- Data referred to by entries in the program header table or section header table

The segments contain information that is needed for run time execution of the file, while sections contain important data for linking and relocation. Any byte in the entire file can be owned by one section at most, and orphan bytes can occur which are unowned by any section.
00000000 7f 45 4c 46 02 01 01 00 00 00 00 00 00 00 00 00 |.ELF............|
00000010 02 00 3e 00 01 00 00 00 c5 48 40 00 00 00 00 00 |..>......H@.....|
Example hexdump of ELF file header[4]
File header
The ELF header defines whether to use 32-bit or 64-bit addresses. The header contains three fields that are affected by this setting and offset other fields that follow them. The ELF header is 52 or 64 bytes long for 32-bit and 64-bit binaries respectively.
| Offset | Size (bytes) | Field | Purpose | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32-bit | 64-bit | 32-bit | 64-bit | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x00 | 4 | e_ident[EI_MAG0] through e_ident[EI_MAG3] | 0x7F followed by ELF(45 4c 46) in ASCII; these four bytes constitute the magic number. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x04 | 1 | e_ident[EI_CLASS] | This byte is set to either 1 or 2 to signify 32- or 64-bit format, respectively. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x05 | 1 | e_ident[EI_DATA] | This byte is set to either 1 or 2 to signify little or big endianness, respectively. This affects interpretation of multi-byte fields starting with offset 0x10. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x06 | 1 | e_ident[EI_VERSION] | Set to 1 for the original and current version of ELF. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x07 | 1 | e_ident[EI_OSABI] | Identifies the target operating system ABI.
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x08 | 1 | e_ident[EI_ABIVERSION] | Further specifies the ABI version. Its interpretation depends on the target ABI. Linux kernel (after at least 2.6) has no definition of it,[6] so it is ignored for statically-linked executables. In that case, offset and size of EI_PAD are 8.
glibc 2.12+ in case e_ident[EI_OSABI] == 3 treats this field as ABI version of the dynamic linker:[7] it defines a list of dynamic linker's features,[8] treats e_ident[EI_ABIVERSION] as a feature level requested by the shared object (executable or dynamic library) and refuses to load it if an unknown feature is requested, i.e. e_ident[EI_ABIVERSION] is greater than the largest known feature.[9] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x09 | 7 | e_ident[EI_PAD] | Reserved padding bytes. Currently unused. Should be filled with zeros and ignored when read. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x10 | 2 | e_type | Identifies object file type.
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x12 | 2 | e_machine | Specifies target instruction set architecture. Some examples are:
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x14 | 4 | e_version | Set to 1 for the original version of ELF. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x18 | 4 | 8 | e_entry | This is the memory address of the entry point from where the process starts executing. This field is either 32 or 64 bits long, depending on the format defined earlier (byte 0x04). If the file doesn't have an associated entry point, then this holds zero. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x1C | 0x20 | 4 | 8 | e_phoff | Points to the start of the program header table. It usually follows the file header immediately following this one, making the offset 0x34 or 0x40 for 32- and 64-bit ELF executables, respectively. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x20 | 0x28 | 4 | 8 | e_shoff | Points to the start of the section header table. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x24 | 0x30 | 4 | e_flags | Interpretation of this field depends on the target architecture. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x28 | 0x34 | 2 | e_ehsize | Contains the size of this header, normally 64 Bytes for 64-bit and 52 Bytes for 32-bit format. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x2A | 0x36 | 2 | e_phentsize | Contains the size of a program header table entry. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x2C | 0x38 | 2 | e_phnum | Contains the number of entries in the program header table. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x2E | 0x3A | 2 | e_shentsize | Contains the size of a section header table entry. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x30 | 0x3C | 2 | e_shnum | Contains the number of entries in the section header table. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x32 | 0x3E | 2 | e_shstrndx | Contains index of the section header table entry that contains the section names. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x34 | 0x40 | End of ELF Header (size). | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Program header
The program header table tells the system how to create a process image. It is found at file offset e_phoff, and consists of e_phnum entries, each with size e_phentsize. The layout is slightly different in 32-bit ELF vs 64-bit ELF, because the p_flags are in a different structure location for alignment reasons. Each entry is structured as:
| Offset | Size (bytes) | Field | Purpose | |||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32-bit | 64-bit | 32-bit | 64-bit | |||||||||||||||||||||||||||||||||||||||
| 0x00 | 4 | p_type | Identifies the type of the segment.
| |||||||||||||||||||||||||||||||||||||||
| 0x04 | 4 | p_flags | Segment-dependent flags (position for 64-bit structure).
| |||||||||||||||||||||||||||||||||||||||
| 0x04 | 0x08 | 4 | 8 | p_offset | Offset of the segment in the file image. | |||||||||||||||||||||||||||||||||||||
| 0x08 | 0x10 | 4 | 8 | p_vaddr | Virtual address of the segment in memory. | |||||||||||||||||||||||||||||||||||||
| 0x0C | 0x18 | 4 | 8 | p_paddr | On systems where physical address is relevant, reserved for segment's physical address. | |||||||||||||||||||||||||||||||||||||
| 0x10 | 0x20 | 4 | 8 | p_filesz | Size in bytes of the segment in the file image. May be 0. | |||||||||||||||||||||||||||||||||||||
| 0x14 | 0x28 | 4 | 8 | p_memsz | Size in bytes of the segment in memory. May be 0. | |||||||||||||||||||||||||||||||||||||
| 0x18 | 4 | p_flags | Segment-dependent flags (position for 32-bit structure). See above p_flags field for flag definitions. | |||||||||||||||||||||||||||||||||||||||
| 0x1C | 0x30 | 4 | 8 | p_align | 0 and 1 specify no alignment. Otherwise should be a positive, integral power of 2, with p_vaddr equating p_offset modulus p_align. | |||||||||||||||||||||||||||||||||||||
| 0x20 | 0x38 | End of Program Header (size). | ||||||||||||||||||||||||||||||||||||||||
Section header
| Offset | Size (bytes) | Field | Purpose | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32-bit | 64-bit | 32-bit | 64-bit | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x00 | 4 | sh_name | An offset to a string in the .shstrtab section that represents the name of this section. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x04 | 4 | sh_type | Identifies the type of this header.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x08 | 4 | 8 | sh_flags | Identifies the attributes of the section.
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x0C | 0x10 | 4 | 8 | sh_addr | Virtual address of the section in memory, for sections that are loaded. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x10 | 0x18 | 4 | 8 | sh_offset | Offset of the section in the file image. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x14 | 0x20 | 4 | 8 | sh_size | Size in bytes of the section in the file image. May be 0. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x18 | 0x28 | 4 | sh_link | Contains the section index of an associated section. This field is used for several purposes, depending on the type of section. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x1C | 0x2C | 4 | sh_info | Contains extra information about the section. This field is used for several purposes, depending on the type of section. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x20 | 0x30 | 4 | 8 | sh_addralign | Contains the required alignment of the section. This field must be a power of two. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x24 | 0x38 | 4 | 8 | sh_entsize | Contains the size, in bytes, of each entry, for sections that contain fixed-size entries. Otherwise, this field contains zero. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| 0x28 | 0x40 | End of Section Header (size). | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Tools
readelfis a Unix binary utility that displays information about one or more ELF files. A free software implementation is provided by GNU Binutils.elfutilsprovides alternative tools to GNU Binutils purely for Linux.[11]elfdumpis a command for viewing ELF information in an ELF file, available under Solaris and FreeBSD.objdumpprovides a wide range of information about ELF files and other object formats.objdumpuses the Binary File Descriptor library as a back-end to structure the ELF data.- The Unix
fileutility can display some information about ELF files, including the instruction set architecture for which the code in a relocatable, executable, or shared object file is intended, or on which an ELF core dump was produced.
Applications
Unix-like systems
The ELF format has replaced older executable formats in various environments. It has replaced a.out and COFF formats in Unix-like operating systems:
Non-Unix adoption
ELF has also seen some adoption in non-Unix operating systems, such as:
- OpenVMS, in its Itanium and amd64 versions[14]
- BeOS Revision 4 and later for x86 based computers (where it replaced the Portable Executable format; the PowerPC version stayed with Preferred Executable Format)
- Haiku, an open source reimplementation of BeOS
- RISC OS[15]
- Stratus VOS, in PA-RISC and x86 versions
- SkyOS
- Fuchsia OS
- Z/TPF
- HPE NonStop OS[16]
- Deos
Microsoft Windows also uses the ELF format, but only for its Windows Subsystem for Linux compatibility system.[17]
Game consoles
Some game consoles also use ELF:
PowerPC
Other (operating) systems running on PowerPC that use ELF:
- AmigaOS 4, the ELF executable has replaced the prior Extended Hunk Format (EHF) which was used on Amigas equipped with PPC processor expansion cards.
- MorphOS
- AROS
- Café OS (The operating system ran on Wii U)
Mobile phones
Some operating systems for mobile phones and mobile devices use ELF:
- Symbian OS v9 uses E32Image[19] format that is based on the ELF file format;
- Sony Ericsson, for example, the W800i, W610, W300, etc.
- Siemens, the SGOLD and SGOLD2 platforms: from Siemens C65 to S75 and BenQ-Siemens E71/EL71;
- Motorola, for example, the E398, SLVR L7, v360, v3i (and all phone LTE2 which has the patch applied).
- Bada, for example, the Samsung Wave S8500.
- Nokia phones or tablets running the Maemo or the Meego OS, for example, the Nokia N900.
- Android uses ELF .so (shared object[20]) libraries for the Java Native Interface. With Android Runtime (ART), the default since Android 5.0 "Lollipop", all applications are compiled into native ELF binaries on installation.[21] It also possible to use native Linux software from package managers like Termux, or compile them from sources via Clang or GCC, that also available in repositories.
Some phones can run ELF files through the use of a patch that adds assembly code to the main firmware, which is a feature known as ELFPack in the underground modding culture. The ELF file format is also used with the Atmel AVR (8-bit), AVR32[22] and with Texas Instruments MSP430 microcontroller architectures. Some implementations of Open Firmware can also load ELF files, most notably Apple's implementation used in almost all PowerPC machines the company produced.
Specifications
- Generic:
- System V Application Binary Interface Edition 4.1 (1997-03-18)
- System V ABI Update (October 2009)
- AMD64:
- Arm:
- IA-32:
- IA-64:
- Itanium Software Conventions and Runtime Guide (September 2000)
- M32R:
- M32R ELF ABI Supplement Version 1.2 (2004-08-26)
- MIPS:
- System V ABI, MIPS RISC Processor Supplement
- MIPS EABI documentation Archived 2012-04-01 at the Wayback Machine (2003-06-11)
- Motorola 6800:
- PA-RISC:
- ELF Supplement for PA-RISC Version 1.43 (October 6, 1997)
- PowerPC:
- System V ABI, PPC Supplement
- PowerPC Embedded Application Binary Interface 32-Bit Implementation (1995-10-01)
- 64-bit PowerPC ELF Application Binary Interface Supplement Version 1.9 (2004)
- RISC-V:
- SPARC:
- S/390:
- zSeries:
- Symbian OS 9:
The Linux Standard Base (LSB) supplements some of the above specifications for architectures in which it is specified.[23] For example, that is the case for the System V ABI, AMD64 Supplement.[24][25]
86open
86open was a project to form consensus on a common binary file format for Unix and Unix-like operating systems on the common PC compatible x86 architecture, to encourage software developers to port to the architecture.[26] The initial idea was to standardize on a small subset of Spec 1170, a predecessor of the Single UNIX Specification, and the GNU C Library (glibc) to enable unmodified binaries to run on the x86 Unix-like operating systems. The project was originally designated "Spec 150".
The format eventually chosen was ELF, specifically the Linux implementation of ELF, after it had turned out to be a de facto standard supported by all involved vendors and operating systems.
The group began email discussions in 1997 and first met together at the Santa Cruz Operation offices on August 22, 1997.
The steering committee was Marc Ewing, Dion Johnson, Evan Leibovitch, Bruce Perens, Andrew Roach, Bryan Wayne Sparks and Linus Torvalds. Other people on the project were Keith Bostic, Chuck Cranor, Michael Davidson, Chris G. Demetriou, Ulrich Drepper, Don Dugger, Steve Ginzburg, Jon "maddog" Hall, Ron Holt, Jordan Hubbard, Dave Jensen, Kean Johnston, Andrew Josey, Robert Lipe, Bela Lubkin, Tim Marsland, Greg Page, Ronald Joe Record, Tim Ruckle, Joel Silverstein, Chia-pi Tien, and Erik Troan. Operating systems and companies represented were BeOS, BSDI, FreeBSD, Intel, Linux, NetBSD, SCO and SunSoft.
The project progressed and in mid-1998, SCO began developing lxrun, an open-source compatibility layer able to run Linux binaries on OpenServer, UnixWare, and Solaris. SCO announced official support of lxrun at LinuxWorld in March 1999. Sun Microsystems began officially supporting lxrun for Solaris in early 1999,[27] and later moved to integrated support of the Linux binary format via Solaris Containers for Linux Applications.
With the BSDs having long supported Linux binaries (through a compatibility layer) and the main x86 Unix vendors having added support for the format, the project decided that Linux ELF was the format chosen by the industry and "declare[d] itself dissolved" on July 25, 1999.[28]
FatELF: universal binaries for Linux
FatELF is an ELF binary-format extension that adds fat binary capabilities.[29] It is aimed for Linux and other Unix-like operating systems. Additionally to the CPU architecture abstraction (byte order, word size, CPU instruction set etc.), there is the potential advantage of software-platform abstraction e.g., binaries which support multiple kernel ABI versions. As of 2021, FatELF has not been integrated into the mainline Linux kernel.[30][31][32]
See also
- Application binary interface
- Comparison of executable file formats
- DWARF – a format for debugging data
- Intel Binary Compatibility Standard
- Portable Executable – format used by Windows
- vDSO – virtual DSO
- Position-independent code
References
- Tool Interface Standard (TIS) Executable and Linking Format (ELF) Specification Version 1.2 (May 1995)
- Tool Interface Standard (TIS) Portable Formats Specification Version 1.1 (October 1993)
- System V Application Binary Interface Edition 4.1 (1997-03-18)
- "Available lexers — Pygments". pygments.org.
- "ELF Header". Sco.com. July 2000. Retrieved 2014-02-07.
- "LXR linux/include/linux/elf.h". linux.no. Retrieved 27 April 2015.
- "glibc 2.12 announce".
- "sourceware.org Git - glibc.git/blob - libc-abis".
- "sourceware.org Git - glibc.git/blob - sysdeps/gnu/ldsodefs.h". Archived from the original on 2021-03-07. Retrieved 2019-10-28.
- "Program Header". Sco.com. July 2000. Retrieved 2017-04-05.
- "elfutils". sourceware.org. Retrieved 30 April 2017.
- "Binary Formats". Archived from the original on 2019-03-31. Retrieved 2019-03-31.
- "MinixReleases – Minix Wiki". Wiki.minix3.org. Archived from the original on 2013-03-30. Retrieved 2014-01-19.
- "Archived copy" (PDF). Archived from the original (PDF) on 2020-09-15. Retrieved 2016-10-19.
{{cite web}}: CS1 maint: archived copy as title (link) - "GCCSDK – RISC OS". Riscos.info. 2012-04-22. Retrieved 2014-01-19.
- "Guardian Programmer's Guide" (PDF). Hewlett Packard Enterprise. Archived from the original (PDF) on 2018-05-30. Retrieved 2018-05-30. p. 44 archived from the original Archived 2018-05-30 at the Wayback Machine on 2018-5-30
- Foley, Mary Jo. "Under the hood of Microsoft's Windows Subsystem for Linux | ZDNet". ZDNet. Retrieved 2016-08-19.
- PlayStation Portable use encrypted & relocated ELF : PSP
- Symbian OS executable file format
-
Rosen, Kenneth; Host, Douglas; Klee, Rachel; Rosinski, Richard (2007). UNIX: The Complete Reference (2 ed.). McGraw Hill Professional. p. 707. ISBN 9780071706988. Retrieved 2017-06-08.
Dynamically linked libraries are also called shared objects (.so).
- Thomas, Romain. "Android formats". Quarks Lab. Archived from the original on 16 Feb 2023. Retrieved 17 Jan 2023.
- "Chapter 4: Object Files", System V Application Binary Interface, 2009-10-26, e_machine
- "LSB Referenced Specifications". linuxfoundation.org. Retrieved 27 April 2015.
- "Executable and Linking Format (ELF)". linuxfoundation.org. Retrieved 27 April 2015.
- "Introduction". linuxfoundation.org. Retrieved 27 April 2015.
- Leibovitch, Evan (1997-12-23). "86Open Frequently-Asked Questions". Archived from the original on 2007-03-11. Retrieved 2007-06-06.
- Record, Ronald (1998-05-21). "Bulletin on status of 86open at SCO". Archived from the original on 2008-12-08. Retrieved 2008-05-06.
- Leibovitch, Evan (1999-07-25). "The86open Project – Final Update". Archived from the original on 2007-02-27. Retrieved 2007-05-06.
- Gordon, Ryan. "fatelf-specification v1". icculus.org. Retrieved 2010-07-25.
- Gordon, Ryan. "FatELF: Turns out I liked the uncertainty better". icculus.org. Retrieved 2010-07-13.
- Holwerda, Thom (2009-11-03). "Ryan Gordon Halts FatELF Project". osnews.com. Retrieved 2010-07-05.
- Brockmeier, Joe (June 23, 2010). "SELF: Anatomy of an (alleged) failure". Linux Weekly News. Retrieved 2011-02-06.
Further reading
- Levine, John R. (2000) [October 1999]. Linkers and Loaders. The Morgan Kaufmann Series in Software Engineering and Programming (1 ed.). San Francisco, USA: Morgan Kaufmann. ISBN 1-55860-496-0. OCLC 42413382. Archived from the original on 2012-12-05. Retrieved 2020-01-12. Code: Errata:
- Drepper, Ulrich (2006-08-20). "How To Write Shared Libraries" (PDF). 4.0. Retrieved 2007-06-20.
{{cite journal}}: Cite journal requires|journal=(help) - An unsung hero: The hardworking ELF by Peter Seebach, December 20, 2005, archived from the original on February 24, 2007
- LibElf and GElf - A Library to Manipulate ELf Files at the Wayback Machine (archived February 25, 2004)
- The ELF Object File Format: Introduction, The ELF Object File Format by Dissection by Eric Youngdale (1995-05-01)
- A Whirlwind Tutorial on Creating Really Teensy ELF Executables for Linux by Brian Raiter
- ELF relocation into non-relocatable objects by Julien Vanegue (2003-08-13)
- Embedded ELF debugging without ptrace by the ELFsh team (2005-08-01)
- Study of ELF loading and relocs by Pat Beirne (1999-08-03)
External links
- FreeBSD Handbook: Binary formats (archived version)
- FreeBSD elf(5) manual page
- NetBSD ELF FAQ
- Linux elf(5) manual page
- Oracle Solaris Linker and Libraries Guide
- The ERESI project : reverse engineering on ELF-based operating systems Archived 2021-03-14 at the Wayback Machine
- Linux Today article on 86open July 26, 1999
- Announcement of 86open on Debian Announce mailing list October 10, 1997, Bruce Perens
- Declaration of Ulrich Drepper (PDF) in The SCO Group vs IBM, September 19, 2006
- 86open and ELF discussion Archived 2019-02-01 at the Wayback Machine on Groklaw, August 13, 2006