Fakesysdef
Trojan:Win32/FakeSysdef, originally dispersed as an application called "HDD Defragmenter" hence the name "FakeSysdef" or "Fake System Defragmenter", is a Trojan targeting the Microsoft Windows operating system that was first documented in late 2010.[1]
 | |
| Technical name | Trojan:Win32/FakeSysdef |
|---|---|
| Aliases |
|
| Family | Malware |
| Type | Computer virus |
| Subtype | Trojan |
| Isolation | 2010 |
Win32/FakeSysdef manifests as one or more of an array of programs that purport to scan one's computer for hardware failures related to system memory, hard drives and system functionality as a whole. They scan the computer, show false hardware issues, and present a remedy to defrag the hard drives and fine-tune the system performance. They then request the user to make a payment in order to activate the program so the user can download the new updates and to repair the hardware issues.[2]
The fictitious scanning program detects one or more of the most widespread varieties of risks prevalent on the internet today. Everyday numerous fake antivirus and security applications are published and released to unsuspecting end-users via a large assortment of distribution channels. Many times such software turn out to be clones of each other – developed from the same code base but packaged with a unique title and design through the use of a "skin".[3]
The branding strategy may look legitimate to computer users as the names are usually a combination of technical words such as "HDD", "Disk", "Memory" and action words such as "Scanner", "Defragmenter", "Diagnostics", "Repair", and "Fix".[1]
Operation
Users may encounter this kind of threat when they visit websites that attempt to convince them to remove non-existent malware or security risks from their computers by installing the bogus software. The Trojan can also be installed by other malware, drive-by downloads, and when downloading and installing other software. Users may be directed to these sites by way of the following methods:
- Spam emails that contain links or attachments
- pornography sites
- Blogs and forums that are spammed with links to adult videos
- User-generated content spam (e.g. fake videos)
- Malicious banner advertisements
- Unauthorized software (‘warez’)
- Search engine optimization (SEO) poisoning
- Fake torrents or other files on shared networks
- Web pages containing exploits
These programs intentionally misrepresent the security status of a computer by continually presenting fake scan dialog boxes and alert messages that prompt the user to buy the product.
The programs often have an icon in the notification area of the operating system desktop and constantly display pop-up messages alerting the user about fake security issues such as virus infections. These pop-up windows only disappear once the user has purchased the product and the non-existent threats have supposedly been removed from the compromised computer.
If the user decides to purchase the product, they are presented with a form within the application or are redirected to a website that requests credit card information.[3]
Initial infection
The Win32/FakeSysdef installer may arrive in the computer with various file names. When run, the installer drops and injects a DLL file (or sometimes and EXE file) into common processes, for example "EXPLORER.EXE", "WINLOGON.EXE", and "WININET.EXE".
In some instances, the main executable drops both DLL and EXE components. In this case, the EXE is set to run at every Windows restart and the DLL is injected into "EXPLORER.EXE" by the "EXE" component.
To ensure that it automatically runs every time Windows starts, it drops a copy of itself or its EXE component using a random file name into the %APPDATA% folder.[4]
Win32/FakeSysdef may make widespread changes to the system including: modifying several Internet Explorer settings, enabling submitting non-encrypted form data, changing the desktop wallpaper, displaying or hiding all shortcuts, hiding desktop and start menu links, disabling Windows Task Manager, disabling checking for signatures on downloaded programs, setting low risk file types.
Additionally, some Win32/FakeSysdef variants that may terminate running processes during installation and may block launched application after the computer restarts. During the installation process, they may terminate all running processes and force the computer to restart. After the restart, FakeSysdef attempts to block every launched program, and may then display fake error messages offering to fix the problem.[5] It then repeatedly restarts the computer until the user agrees to buy the fake software.[1][6] It then overwrites data on the hard drive/hard drive disk/HDD.
Symptoms
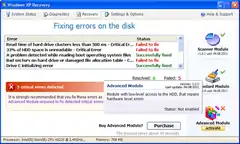
Win32/FakeSysdef displays numerous false alerts indicating system errors while displaying the appearance of scanning the hard disk and defragmenting it, then prompts the user, with a "Fix Errors" button, to buy and activate it to fix discovered errors.
When the "Fix Errors" button is selected, FakeSysdef pretends to scan and defragment the hard disk. It then displays more fake error messages, and tells the user that he needs to purchase an "Advanced Module" for the fix. If the user chooses to do so, the browser opens. It will open a custom web browser where the user can input card information to buy the software.[1]
Removal and detection
Anti-virus software makers responded to the threat of FakeSysdef by adding checks for it in their products. Simple removal of the software enabled by this is sometimes not enough to reverse the damage to configuration files that FakeSysdef was known to edit.
References
- Malware Encyclopedia: Trojan:Win32/FakeSysdef, Microsoft, 2010-11-10, retrieved 2013-03-15
- FakeSysdef, Spyware Remove, 2010-11-30, retrieved 2013-03-15
- Security Response: Trojan.FakeAV, Symantec, 2013-03-13, retrieved 2013-03-19
- MSRT August '11: FakeSysdef, TechNet Blogs, 2011-08-10, retrieved 2013-03-15
- Vincentas (9 July 2013). "Fakesysdef in SpyWareLoop.com". Spyware Loop. Archived from the original on 2 April 2015. Retrieved 28 July 2013.
- Evaluation and extraction of the potent and tricky Fakesysdef Aka Alureon Rootkit, Rapid Whiz, 2012-03-19, retrieved 2013-03-15