Gadget (computer science)
In computational complexity theory, a gadget is a subunit of a problem instance that simulates the behavior of one of the fundamental units of a different computational problem. Gadgets are typically used to construct reductions from one computational problem to another, as part of proofs of NP-completeness or other types of computational hardness. The component design technique is a method for constructing reductions by using gadgets.[1]
Szabó (2009) traces the use of gadgets to a 1954 paper in graph theory by W. T. Tutte, in which Tutte provided gadgets for reducing the problem of finding a subgraph with given degree constraints to a perfect matching problem. However, the "gadget" terminology has a later origin, and does not appear in Tutte's paper.[2][3]
Example
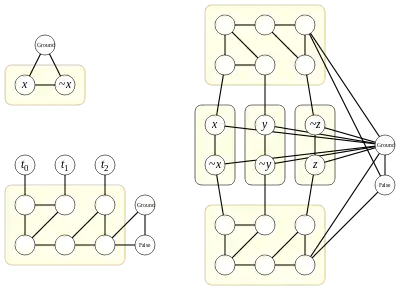
Many NP-completeness proofs are based on many-one reductions from 3-satisfiability, the problem of finding a satisfying assignment to a Boolean formula that is a conjunction (Boolean and) of clauses, each clause being the disjunction (Boolean or) of three terms, and each term being a Boolean variable or its negation. A reduction from this problem to a hard problem on undirected graphs, such as the Hamiltonian cycle problem or graph coloring, would typically be based on gadgets in the form of subgraphs that simulate the behavior of the variables and clauses of a given 3-satisfiability instance. These gadgets would then be glued together to form a single graph, a hard instance for the graph problem in consideration.[4]
For instance, the problem of testing 3-colorability of graphs may be proven NP-complete by a reduction from 3-satisfiability of this type. The reduction uses two special graph vertices, labeled as "Ground" and "False", that are not part of any gadget. As shown in the figure, the gadget for a variable x consists of two vertices connected in a triangle with the ground vertex; one of the two vertices of the gadget is labeled with x and the other is labeled with the negation of x. The gadget for a clause (t0 ∨ t1 ∨ t2) consists of six vertices, connected to each other, to the vertices representing the terms t0, t1, and t2, and to the ground and false vertices by the edges shown. Any 3-CNF formula may be converted into a graph by constructing a separate gadget for each of its variables and clauses and connecting them as shown.[5]
In any 3-coloring of the resulting graph, one may designate the three colors as being true, false, or ground, where false and ground are the colors given to the false and ground vertices (necessarily different, as these vertices are made adjacent by the construction) and true is the remaining color not used by either of these vertices. Within a variable gadget, only two colorings are possible: the vertex labeled with the variable must be colored either true or false, and the vertex labeled with the variable's negation must correspondingly be colored either false or true. In this way, valid assignments of colors to the variable gadgets correspond one-for-one with truth assignments to the variables: the behavior of the gadget with respect to coloring simulates the behavior of a variable with respect to truth assignment. Each clause assignment has a valid 3-coloring if at least one of its adjacent term vertices is colored true, and cannot be 3-colored if all of its adjacent term vertices are colored false. In this way, the clause gadget can be colored if and only if the corresponding truth assignment satisfies the clause, so again the behavior of the gadget simulates the behavior of a clause.
Restricted reductions
Agrawal et al. (1997) considered what they called "a radically simple form of gadget reduction", in which each bit describing part of a gadget may depend only on a bounded number of bits of the input, and used these reductions to prove an analogue of the Berman–Hartmanis conjecture stating that all NP-complete sets are polynomial-time isomorphic.[6]
The standard definition of NP-completeness involves polynomial time many-one reductions: a problem in NP is by definition NP-complete if every other problem in NP has a reduction of this type to it, and the standard way of proving that a problem in NP is NP-complete is to find a polynomial time many-one reduction from a known NP-complete problem to it. But (in what Agrawal et al. called "a curious, often observed fact") all sets known to be NP-complete at that time could be proved complete using the stronger notion of AC0 many-one reductions: that is, reductions that can be computed by circuits of polynomial size, constant depth, and unbounded fan-in. Agrawal et al. proved that every set that is NP-complete under AC0 reductions is complete under an even more restricted type of reduction, NC0 many-one reductions, using circuits of polynomial size, constant depth, and bounded fan-in. In an NC0 reduction, each output bit of the reduction can depend only on a constant number of input bits.[6]
The Berman–Hartmanis conjecture is an unsolved problem in computational complexity theory stating that all NP-complete problem classes are polynomial-time isomorphic. That is, if A and B are two NP-complete problem classes, there is a polynomial-time one-to-one reduction from A to B whose inverse is also computable in polynomial time. Agrawal et al. used their equivalence between AC0 reductions and NC0 reductions to show that all sets complete for NP under AC0 reductions are AC0-isomorphic.[6]
Optimization of gadgets
One application of gadgets is in proving hardness of approximation results, by reducing a problem that is known to be hard to approximate to another problem whose hardness is to be proven. In this application, one typically has a family of instances of the first problem in which there is a gap in the objective function values, and in which it is hard to determine whether a given instance has an objective function that is on the low side or on the high side of the gap. The reductions used in these proofs, and the gadgets used in the reductions, must preserve the existence of this gap, and the strength of the inapproximability result derived from the reduction will depend on how well the gap is preserved.
Trevisan et al. (2000) formalize the problem of finding gap-preserving gadgets, for families of constraint satisfaction problems in which the goal is to maximize the number of satisfied constraints.[7] They give as an example a reduction from 3-satisfiability to 2-satisfiability by Garey, Johnson & Stockmeyer (1976), in which the gadget representing a 3-SAT clause consists of ten 2-SAT clauses, and in which a truth assignment that satisfies 3-SAT clause also satisfies at least seven clauses in the gadget, while a truth assignment that fails to satisfy a 3-SAT clause also fails to satisfy more than six clauses of the gadget.[8] Using this gadget, and the fact that (unless P = NP) there is no polynomial-time approximation scheme for maximizing the number of 3-SAT clauses that a truth assignment satisfies, it can be shown that there is similarly no approximation scheme for MAX 2-SAT.
Trevisan et al. show that, in many cases of the constraint satisfaction problems they study, the gadgets leading to the strongest possible inapproximability results may be constructed automatically, as the solution to a linear programming problem. The same gadget-based reductions may also be used in the other direction, to transfer approximation algorithms from easier problems to harder problems. For instance, Trevisan et al. provide an optimal gadget for reducing 3-SAT to a weighted variant of 2-SAT (consisting of seven weighted 2-SAT clauses) that is stronger than the one by Garey, Johnson & Stockmeyer (1976); using it, together with known semidefinite programming approximation algorithms for MAX 2-SAT, they provide an approximation algorithm for MAX 3-SAT with approximation ratio 0.801, better than previously known algorithms.
References
- Garey, M. R.; Johnson, D. S. (1979), "3.2.3 Component Design", Computers and Intractability: A Guide to the Theory of NP-Completeness, San Francisco, Calif.: W. H. Freeman, pp. 72–74, ISBN 0-7167-1045-5, MR 0519066.
- Szabó, Jácint (2009), "Good characterizations for some degree constrained subgraphs", Journal of Combinatorial Theory, Series B, 99 (2): 436–446, doi:10.1016/j.jctb.2008.08.009, MR 2482961.
- Tutte, W. T. (1954), "A short proof of the factor theorem for finite graphs", Canadian Journal of Mathematics, 6: 347–352, doi:10.4153/CJM-1954-033-3, hdl:10338.dmlcz/101241, MR 0063008.
- Sipser, Michael (1997), Introduction to the Theory of Computation, PWS Publishing Co., p. 260.
- This reduction is described in Goldreich, Oded (2008), Computational Complexity: A Conceptual Perspective, Cambridge University Press, Proposition 2.27, p. 81.
- Agrawal, Manindra; Allender, Eric; Impagliazzo, Russell; Pitassi, Toniann; Rudich, Steven (1997), "Reducing the complexity of reductions", Proceedings of the 29th ACM Symposium on Theory of Computing (STOC '97), pp. 730–738, doi:10.1145/258533.258671. Agrawal, Manindra; Allender, Eric; Rudich, Steven (1998), "Reductions in circuit complexity: an isomorphism theorem and a gap theorem", Journal of Computer and System Sciences, 57 (2): 127–143, doi:10.1006/jcss.1998.1583.
- Trevisan, Luca; Sorkin, Gregory B.; Sudan, Madhu; Williamson, David P. (2000), "Gadgets, approximation, and linear programming", SIAM Journal on Computing, 29 (6): 2074–2097, doi:10.1137/S0097539797328847, MR 1756405.
- Garey, Michael R.; Johnson, David S.; Stockmeyer, Larry (1976), "Some simplified NP-complete graph problems", Theoretical Computer Science: 237–267, doi:10.1016/0304-3975(76)90059-1.