TransApps
TransApps (Transformative Applications) was a program of the Defense Advanced Research Projects Agency (DARPA) of the United States Department of Defense. The goal of the program was to demonstrate rapid development and fielding of secure mobile apps on the battlefield. With its agile and user-centric approach, the DARPA program specifically addressed the limitations of the slow requirements-centric software development cycle followed by many Army programs of record.
The TransApps program created a rapid development and enhancements process within the tactical environment, and embedded a small team of trainers and developers within the deployed military units in Afghanistan, the program also tackled a wide range of issues related to hardware and software security, agile map-imagery distribution and enhancements, combat radio integration, disconnected and connected users, and third party app testing and integration. Unlike a typical DARPA program at the time, the program brought together multiple contractors and Government personnel in a co-located incubator-like environment during the program's lifetime.
By the end of the program, roughly fifty apps were deployed in a secure operational environment.
Timeline
The TransApps Broad Agency Announcement (BAA) was released in March 2010.[1] The BAA noted a range of potential use cases, including tactical battlefield applications, as well as humanitarian missions and disaster recovery. The TransApps program was devised and initially managed by Dr. Mari Maeda – developer of a previous DARPA project, the Tactical Ground Reporting System (TIGR). Many of the existing requirements of the TIGR application provided the foundation for the follow-on baseline requirements for TransApps. These included a renewed emphasis on user-centric development, as well as a focus on security, functionality under limited connectivity, and a broader suite of applications.[2]
TransApps was initially awarded in September 2010 to the Corporation for National Research Initiatives (CNRI), with the focus on building a secure, mobile app store.[3] This was followed a few years later with a contract awarded to Metronome to build out the app store.[4] The app store, simply referred to as the “Marketplace” emphasizes a flexible and extensible environment to meet a wide range of mission needs, within a collaborative development environment to optimize DARPA’s investment.[5] Moreover, it serves as a key component in innovating the acquisition process, expediting the time from application development to mission use. Over time, Metronome has expanded the marketplace to focus on mobile and cyber security as well.[6]
While there has been much success, TransApps initially relied upon the Dell Streak, which was discontinued in 2011. Since then, the TransApps platform has adjusted to function on a range of hardware, including Motorola Xoom, Galaxy Note, and Samsung S4. In addition to security, additional emphasis has also been placed on usability and visualization via the iWarrior SBIR that falls under TransApps.[7] In 2012, TransApps was identified as one of the top 25 C4ISR breakthroughs of the year.[8] In April 2013, DARPA awarded a contract to GXM Consulting to continue to expand the functionality and robustness of the smartphones.[9]
TransApps not only has focused on security abroad, but has also employed the capabilities domestically. TransApps supported first response and law enforcement personnel during the 2013 Presidential Inauguration.[10] That same year, TransApps also was present at the Boston Marathon, providing similar support for first responders, and did so again at the 2014 Boston Marathon. During FY2014, TransApps is working with the Army Nett Warrior Program to fully transition the project to the Army as a program of record.[11]
The TransApps Ecosystem: DARPA-Hard Innovations
The TransApps program pursued novel functionality and security for the operational user, but also pursued a new acquisition paradigm to significantly decrease the time and money from development to operational use. TransApps was required to create a modern mobile capability within the constraints of a tactical operating environment. The applications are the most visible feature, and required and benefited from constant feedback from the user community. However, the vast majority of the innovations dealt both with expediting the acquisition process to deliver timely capabilities for the warfighter, as well as handling the network/security and operations/logistics within a tactical environment.
Altering the Acquisition Paradigm
The normal DARPA acquisition process involves three to four months of selecting a winning proposal, an additional three to four months to negotiate the contract, and then continuing with the same vendor for three to five years. In contrast, the TransApps program sought to replicate best practices from the commercial world, including an integrated and collaborative working environment indicative of a start-up, and quickly moving from development to mission use.
The TransApps program pursued a “warfighter empowered acquisition” mentality to field capabilities faster and in sync with current warfighter requirements.[12] TransApps sought to establish a new acquisition model that can circumvent the standard bureaucratic delays with developing and fielding capabilities. This new business model required navigating both technological as well as bureaucratic hurdles to quickly field the new applications.[13] In 2012, Maeda, then the deputy director, Defense Sciences Office at DARPA said, "Today, we have 3-to-4000 users in an ongoing program in Afghanistan using a secure, robust Android handheld device. We roll out new capabilities every three to four months, from new apps to new server capabilities."[14]
TransApps not only pursued a new model for acquisition, but also represented a shift in development processes, one that entailed placing the engineers in the users’ environment. In 2012, a TransApps team, including computer scientists, spent nine months in Afghanistan to gather user requirements, and develop and test applications. They also were able to reach back to the larger TransApps team in the United States to expedite development and quickly provide capabilities to tactical users.[15]
Instead of fielding capabilities at the end of the development process, the TransApps pilot efforts gathered immediate feedback, identifying quickly which requirements were met, technical bugs in devices, as well as ideas for the next development cycles based explicitly on user feedback.[16] DARPA has worked with the U.S. Army Research, Development, and Engineering Command’s Communications-Electronics Center (CERDEC) to ensure downrange support and mission-driven development.[17] As Doran Michels, the DARPA Program Manager in charge of TransApps, explained in a December 2013 press release, “We wanted soldiers to drive the development of the applications so we knew the apps could evolve in real time with dynamic mission requirements.”[18]
Less than a year after awarding the TransApp program, a pilot program was underway with the 3rd Brigade of the 10th Mountain Division in Afghanistan to test the mobile devices running the Android OS. In addition to testing the security, the TransApps team also developed a dozen applications by mid-Fall 2011. This pilot effort helped harden the requirement for functionality within disconnected as well as connected environments.[19] The development process can be viewed as a ‘wireless to the edge’ approach, tightly integrating with potential tactical users. This has provided the opportunity to ensure usability and applicability across an array of use cases. The initial requirements focused on high-resolution mobile imagery and additional ways to interact with and navigate the geospatial applications. Once these initial requirements were satisfied, the users immediately began identifying and asking for additional functionality. In many instances, users identified novel use cases that extended beyond the original intent, and thus expanded the utility of the mobile devices.[20] For instance, although the handheld devices first emerged as a way to explore and interact with detailed maps, it soon became apparent that they could also be used as collection platforms.[18]
The involvement of the user community had operational impacts as early as 2012. According to a Wall Street Journal article, "During a battle in a village near Kandahar, Afghanistan, Lt. Kevin Pelletier used a tablet computer with a custom map application to direct soldiers' movements. As thousands of rounds flew through the village near Kandahar, Lt. Pelletier used the device to more quickly direct the movement of his soldiers. Two days later, the village was cleared with zero casualties." Not only did this process impact immediate operational support, but also helped set the foundation for scaling the capability. The reiterative process between user feedback and development efforts enabled the quick escalation from application within smaller units to company, battalion and then brigade levels.[21] Similarly, Major Tim Terese has used the TransApps smartphone to plan operations in Afghanistan, and called it a, “vast improvement in dismounted situational awareness.”[22]
Security & the Tactical Environment
TransApps focuses on developing functionality on an Android platform, emphasizing the requirement to securely function within limited bandwidth environments as well as without connectivity.[23] Android was chosen over iOS systems due to the open architecture that would enable modifications for developers to create a secure kernel for the operating system.[24] DARPA customized the Android kernel, hardening the stack and implementing the ability to check for data integrity. The stack included a custom-modified Android-operating system and Linux kernels, with a security stack that includes protection for data at rest, data in transit, authentication, and app vetting and control.[18]
Unlike in the commercial world, where security resides on the network, due to the patchy communications in theater, TransApps needed to adjust to ensure security resided within the phone itself. According to Michels, the security is so robust that “it would take several CPU years to crack the log-in password on a military Android.” TransApps also had to ensure that the devices could integrate with the existing military infrastructure. The smartphones needed software that could recognize and function within the particular data constraints of whatever waveform was used, be it PRC-152, MPU4 or Satcom.[25] This is essential, as data outages occur often in theater, and the handheld devices needed to contain the essential data in the event of a communications loss.[26] The secure system uses military radios rather than commercial, wifi or cellular networks, according to DARPA.[27]
TransApps expanded the emphasis on security in 2012, and included the Mobile Armour program. Awarded in June 2012, the Mobile Armour component intends to secure both smartphones and tablet devices in the battlefield.[6] Similarly, Vanderbilt’s ISIS research lab has implemented a means to securely connect the smartphones to military-grade radios to secure chat, video, text and blue force tacking.[28]
App Testing Portal
Working together, the National Institute of Standards and Technology(NIST) and George Mason have run 200,000 applications through application testing software and evaluation of the various technological requirements of distinct application.[29] As a senior researcher at NIST, Tom Karygiannis worked on TransApps and other government programs to help inform NIST’s 2012 mobile security guidelines.[30] In addition, not all of the NIST’s findings were security related, but also addressed issues such as the impact of the application color schema on battery life. According to Jeff Voas, “We can’t send them out on a mission where some application, because it’s got a really red screen, sucks the battery dry and the phone’s only good for a couple of hours as opposed to the 16-hour mission.”[31] These nuances of an operating environment added to the complexity and drove innovation within the security and hardware of the mobile phones. For instance, it was imperative that information could not be obtained via lost or stolen devices. Invincea was awarded a grant to test security along these lines in Afghanistan with 3,000 soldiers. Part of this effort was to ensure that adversaries could not capture information on the devices, while also isolating malicious Web Apps from seemingly harmless sites to take control of the device.[32]
TransApps addressed the inter-app security layer through the FUSE project, which focused on defending against data exfiltration by multiple colluding apps. The FUSE app analysis tool helped compute over-approximations of data intent calls without any false negatives. The project also evaluated the Java bytecode as part of the overarching feasibility study for the TransApps project.[33]
Functional App Testing
DARPA has designed and implemented evaluation and testing strategies for the platform. This includes the functionality of the applications, software-hardware interactions, as well as the online application marketplace.[34] NIST also conducted functional regression testing and quantitative performance testing in the realms of platform integration, client-based applications, and network technologies.[35]
Given the technical constraints and functional requirements, the app testing required a range of security, functional and hardware testing. App testing included testing for different users with different permission levels, various browsers, ease of navigation and use, as well as a range of additional tests targeted at data collection and GPS accuracy. It also included testing on client-based capabilities as well as user-centered testing for bugs, news features, and crashes.[36]
TransApps became part of a larger effort by the NIST to instantiate app testing guidelines within a secure environment. As Tom Karygiannis noted, the NIST produced voluntary guidelines for the government on how to “vet and test mobile apps before you deploy them. It doesn't give you a go or no-go or red light, green light type of thing, but it gives you an idea of what you should test for. Then, in turn, you would need your own security analyst to decide in your environment whether that's acceptable or not."[37]
Applications
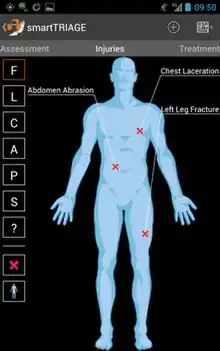
TransApps initially identified several key areas for application development, including: blue-force tracking, speech recognition, cultural training, human terrain mapping, mission planning and biometrics.[12] The initial requirements focused on geospatial mapping capabilities. For instance, a heat map enabled soldiers during pre-mission briefings to see where they spent their time on patrol, the most frequently used routes, and which areas were underrepresented.[38] The TransHeat app utilizes algorithms to process travel routes, and visually depict for the soldiers the frequency by which they travel each route. This can assist soldiers in taking alternative routes, and provide less predictability in their behavior, which in turn can help them avoid ambushes, IEDs and roadside bombers.[18] A variety of applications also focus on enabling soldiers to collaborate and share data, track operations, and debrief and replay missions.[39] At the request of the National Park Service, TransApps created SMART Triage – an app that lets first responders document the characteristics of the injured personnel, and log injuries and treatments. It depicts a 3-D mannequin that can be annotated with medications and other treatments.
Additional applications assist in the search and rescue mission. The Search and Rescue Application (SARApp) allows users to search and collect data, including georeferencing and time stamps, to facilitate reporting and response management. This includes a range of data, such as photos, imagery, and audio recordings, which are displayed on a map.[40] The smartphone also includes language translation capabilities across a range of language.[41] Finally, an app was created during one of the TransApps hackathons to enable soldiers to track their daily workouts and caloric intake. Called GPX Fitness, the app was fully functional within six days and was created by a team of three developers.[42] In sum, these handheld devices possess a range of functionality, including maps, collaboration, collection and even text messaging. A unit Operations Officer stated, “I feel that this device will be able to replace 4 or 5 different things they need to carry on mission.”[43]

Download Presentation Archived 2014-09-03 at the Wayback Machine
Plug-in architecture framework
In her testimony to the House of Representatives' Subcommittee on Intelligence, Emerging Threats, and Capabilities Arati Prabhakar, the DARPA director, described the TransApps plug-in architecture framework as creating, “a new agile development process, integration framework, and customized test cycles to allow rapid development of new applications, with new features and enhancements deployed quickly based on Soldiers’ evolving requirements. When Soldiers need new apps, they can get them quickly – sometimes the very next day. This is a radical departure from how they had been operating. The TransApps ecosystem bridges old and new, allowing future technologies to work seamlessly with legacy radios and information systems. By endowing commercial off-the-shelf (COTS) smartphones with custom multilayered security and agile development processes modified for the tactical community, TransApps is creating a scalable and sustainable infrastructure template.”[44] This plug-in architecture framework was designed to ensure the applications work together seamlessly, with the ability of the entire system to merge into the existing operational architecture. Moreover, the open application programming interfaces (API) emphasize the ability of third-party apps to plug and play into the environment. For instance, more than 30% of the applications include third-party libraries, some of which download and run code from remote servers.[45]
Mobile Imagery Tools
Dr. Arati Prabhakar, the DARPA director, has noted that until recently soldiers have historically relied on fairly primitive mapping capabilities in the field. That is, soldiers have relied largely on paper maps, written notes and reference materials and voice radio transmissions to carry out their missions. With TransApps, users can now update imagery, such as new bridges, unique structures or demographic information within a TransApps mapping capability.[46] Current, high-resolution imagery is essential in disconnected environments. Collection date becomes an extremely important piece of meta-data to gain the trust of the users. Also, unlike other environments, the map imagery could not be streamed, but rather must be loaded onto the SD card, which also limits the amount of imagery that can be loaded.
In order to expedite the imagery provisioning process, TransApps developed Tile Generator, which enables users to load common imagery formats into a viewer and crop the image, and only releases CPU power based on the user’s requirements to help extend the battery life. Similarly, the PanthrTiles manage a large cache of tiles and incorporates new tiles based on the Tile Generator’s output. Future releases will also provide the ability to output to the new OGC GeoPackage specification as a container.[47]
The TransApps also designed map features such that they are resident at all times on the handheld devices. The various interactive features enable soldiers to navigate or follow mission plans or track environmental features. The map imagery sets can be easily customizable for specific missions. Moreover, the information gathered in theater can be shared to ensure that user-created data does not remain inaccessible to others.[18] The mission-planning tools allow soldiers to review the presence of any man-made objects, obstacles, or known areas for avoidance, such as IEDs. Soldiers can also review the locations of previous missions and attacks within the general vicinity.[39]
The DARPA TransApps program has collaborated extensively with other agencies, such as the National Geospatial-Intelligence Agency (NGA) and Naval Research Laboratory (NRL), as well as geo-spatial data providers such as Digital Globe, to bring imagery to mobile devices. Michels has noted, “We have a number of excellent relationships now with organizations like the Army Geospatial Center(AGC), NGA and NRL,” he added, “and we would not have been successful without these thriving partnerships.”[18] Thanks to these partnerships, TransApps has helped socialize standard imagery formats for mobile applications, and leverages other agencies’ innovations, such as NRL’s GHub Sync for dissemination.
Technical Community Outreach
TransApps has reached out to academia, and the public and private sectors to help bring commercial-quality innovation to the public sector. TransApps has benefited from a cross-pollination of people and ideas as part of the public-private partnership.[48] This has occurred both within the TransApps team, but also through outreach to the community for feedback. Additional industry outreach includes various presentations, some of which are listed below.
- Smartphones and Handheld Devices for Defense and Homeland Security, Washington, DC, October 2013 Archived 2014-09-03 at the Wayback Machine;
- 3_Lack.ashx+&cd=87&hl=en&ct=clnk&gl=usSecuring Android Mobile Devices for the Tactical User, April 2012;
- NIST Mobile Device Security Technical Exchange Meeting, January 2012;
- Forthcoming: Mission Command, June 2014;
- Homeland Infrastructure Foundation-Level Data Working Group, September 2013;
- Command and Control Summit, July 2011;
- Mobile Multimedia/Image Processing, Security and Applications, April 2013;
- International Test and Evaluation Association, Annual Conference, 2013 Archived 2014-09-03 at the Wayback Machine;
- Cyber Endeavor: Operations in Cloud and Cellular Networks, Naval Postgraduate School, Monterrey, CA, June 2012.
There also is a growing body of literature related to findings and innovations associated with TransApps. These include:
- Brian A. Weiss, Lisa Fronczek, Emile Morse, Zeid Kootbally, and Craig Schlenoff. 2013,"Performance Assessments of Android-powered Military Applications Operating on Tactical Handheld Devices," From Conference Volume 8755, Mobile Multimedia/Image Processing, Security, and Applications 2013, Sos S. Agaian; Sabah A. Jassim; Eliza Y. Du, Baltimore, Maryland, USA | April 29, 2013.
- D.P. Iracleous, A. Kollan, D. Rigas, 2013, "Cooperative Sensing in Distributed Military Environment Using Smart Devices," Recent Advances in Telecommunication and Circuit Design.
- Scott Scheff, Tristan Plank, John Wilson, and Angelia Sebok. 2013. "Developing Visualization Techniques for Improved Information Comprehension and Reduced Cognitive Workload," Foundations on Augmented Cognition, Lecture Notes in Computer Science Volume 8027.
- Mary R. Schurgot, Jairo Estebany, Lloyd Greenwald, Yang Guoy, Mark Smithy, David Stott, Matteo Varvelloy and Limin Wangy. Providing Local Content Discovery and Sharing in Mobile Tactical Networks. 2013. Military Communications Conference, MILCOM 2013-2013 IEEE. Pgs. 1506-11.
- Len Bass, Nanette Brown, Gene Cahill, William Casey, Sagar Chaki, Cory Cohen, Dionisio de Niz, David French, Arie Gurfinkel, Rick Kazman, Ed Morris, Brad Myers, William Nichols, Robert L. Nord, Ipek Ozkaya, Raghvinder S. Sangwan, Soumya Simanta, Ofer Strichman, Peppo Valetto. Results of SEI Line-Funded Exploratory New Starts Projects. Technical Report. CMU/SEI-2012-TR-004. 2013.
- Jonathon Williams. "A Data Distribution System for Mobile Devices," MS in Computer Science Thesis, Vanderbilt University. 2011.
- A. Shah, An Kyoungho, A. Gokhale, and J. White. "Maximizing Service Uptime of Smartphone-Based Distributed Real-Time and Embedded Systems," Object/Component/Service-Oriented Real-Time Distributed Computing (ISORC), 2011 14th IEEE International Symposium.
Other Military Mobile-Based Efforts
The initial TransApps effort was not without controversy, as it followed the Army’s “Apps for the Army” initiative.[49] A fiscal year 2011 National Defense Authorization Act Report (p. 197-98) emphasized its preference for the “Apps for Army” initiative due to the greater proximity of the Army Chief Information Officer to the warfighter’s operational gaps and needs. The report also expressed concerns about duplication of efforts and the need to deconflict development between the two projects.[50] TransApps was one of almost two dozen DoD mobile application efforts in 2011 including systems such as General Dynamic’s GD 300, the Army’s Relevant ISR to the Edge (RITE), and The Joint Tactical Radio System (JTRS).
Similarly, the Land Warrior project reflects a compilation of 20 years of research and development by the US Army, but was cancelled in 2007, before reinstatement in 2008.[51] Many of the key attributes of the project were identified in 1991, and focused on enhancing situational awareness and a seamless communications network in theater.[52] The Nett Warrior project is a key part of the next generation functionality of the reinstated Land Warrior effort.[53] Pegged for development beginning in 2009, Nett Warrior had an estimated total cost of $1,489.6 million.[54] Prior to the scaled back version, the project is estimated to have cost $2 billion for 74,000 sets of equipment according to a 2012 GAO report.[55] It initially received harsh user feedback, much of which noted the inability to function in limited bandwidth environments, size and weight, and restricted functionality when bandwidth did exist.[56] In FY13, NettWarrior was listed as an Army priority modernization program, and was allocated $150 million.[57]
Techylog
The gap between the two projects may be reconciled. According to John Willison, Director, Command, Power and Integration Directorate, U.S. Army RDECOM, the Army, they have brokered a deal to serve as a bridge between the Nett Warrior and the TransApps programs. The Nett Warrior effort relies on radios within the Joint Battle Command Platform, while TransApps maintains an unconstrained architecture and environment with access to secure military radios. He notes that, at some point, the Army will decide which platform to proceed with, but it may not be an either-or scenario.[58] Similarly, as a recent study pointed out, there is a need for a holistic approach for the tactical use of mobile technology. For instance, there is a need for the integration of TransApps with the Last Tactical Mile (LG3), as well as to provide direct network access to truly replicate the ‘smart phone’ experience.[59]
References
- "SAM.gov | Home". sam.gov.
- "DARPA focuses on technology for national security". Archived from the original on September 5, 2014. Retrieved August 28, 2014.
- Cooney, Michael (September 8, 2010). "Military mobile apps store gets $6.4M to open". Network World. Retrieved March 28, 2023.
- "StackPath".
- "Archived copy". Archived from the original on September 3, 2014. Retrieved August 28, 2014.
{{cite web}}: CS1 maint: archived copy as title (link) - "IAO & Darpa News Page6". Archived from the original on October 13, 2014. Retrieved August 28, 2014.
- Ante, Spencer E. (September 4, 2012). "Military Takes Apps to War". Wall Street Journal.
- "Defense News".
- "StackPath".
- Weiss, Brian A.; Fronczek, Lisa; Morse, Emile; Kootbally, Zeid; Schlenoff, Craig (2013). "Performance assessments of Android-powered military applications operating on tactical handheld devices". In Agaian, Sos S; Jassim, Sabah A; Du, Eliza Y (eds.). Mobile Multimedia/Image Processing, Security, and Applications 2013. p. 875504. Bibcode:2013SPIE.8755E..04W. doi:10.1117/12.2014771. S2CID 55941907.
{{cite book}}:|journal=ignored (help) - "Archived copy". Archived from the original on February 24, 2015. Retrieved December 6, 2014.
{{cite web}}: CS1 maint: archived copy as title (link) - "DARPA Apps Program Generates 'Overwhelming' Response - Blog". Archived from the original on October 21, 2011. Retrieved August 28, 2014.
- For an overview of some of the hurdles and lessons learned from DoD acquisition, see: http://www.aei.org/speech/foreign-and-defense-policy/defense/dhs-acquisition-practices-improving-outcomes-for-taxpayers-using-defense-and-private-sector-lessons-learne/
- "Army's top signal officer: Everything is network dependent". www.army.mil. Retrieved March 28, 2023.
- "Defense News".
- http://www.aerotechnews.com/news/2013/11/18/darpa-focuses-on-technology-for-national-security Archived 2014-09-05 at the Wayback Machine http://www.defensenews.com/article/20120525/C4ISR01/305250007/DARPA-Device-Lauded-by-U-S-Soldiers-Afghanistan Archived 2014-08-28 at archive.today
- http://armyalt.va.newsmemory.com/rss.php?date=20120406&edition=Army+AL%26T+Magazine&subsection=Field+Expedient&page=118alt2012april-june_fieldexpedient.pdf.0&id=art_0.xml&device=
- "News Archive". Archived from the original on January 12, 2014.
- "DARPA's Transformative Apps program drives military's move toward Android devices -- GCN". Archived from the original on September 3, 2014. Retrieved August 28, 2014.
- "Archived copy" (PDF). Archived from the original (PDF) on September 3, 2014. Retrieved August 28, 2014.
{{cite web}}: CS1 maint: archived copy as title (link) - http://seekingalpha.com/article/867571-military-ops-a-new-market-for-these-5-tech-stocks, citing the article: Spencer E. Ante. "Military Takes Apps to War: Soldiers Use Mobile Devices for Mapping, Networking, Virtual Lineups." The Wall Street Journal, September 4, 2012.
- "Defense News".
- "DARPA to build military App Store, battlefield 3G • The Register". The Register.
- "Tactical apps arrive on Androids in Afghanistan". December 12, 2013.
- "How DARPA delivers tactical apps to mobile devices in the field | C4ISR & Networks | c4isrnet.com". Archived from the original on September 3, 2014. Retrieved August 28, 2014.
- "DARPA's Transformative Apps program drives military's move toward Android devices -- GCN". Archived from the original on September 3, 2014. Retrieved August 28, 2014.
- "DARPA's Transformative Apps program drives military's move toward Android devices -- FCW". Archived from the original on August 29, 2016. Retrieved August 28, 2014.
- "Researchers work to secure military smartphones". Fox News. March 24, 2015.
- "National Security Agency Plans Smartphone Adoption". February 3, 2012.
- "NIST Issues New Mobile Security Guidelines".
- "Fierce Wireless Homepage | Fierce Wireless".
- Android security usatoday.com July 1, 2012
- "FUSE: Inter-Application Security for Android" (PDF). gilith.com. Retrieved September 25, 2023.
- "military power applications: Topics by WorldWideScience.org". worldwidescience.org. Retrieved September 25, 2023.
- Weiss, Brian A.; Fronczek, Lisa; Morse, Emile; Kootbally, Zeid; Schlenoff, Craig (2013). Agaian, Sos S; Jassim, Sabah A; Du, Eliza Y (eds.). "Performance assessments of Android-powered military applications operating on tactical handheld devices". Mobile Multimedia/Image Processing. Mobile Multimedia/Image Processing, Security, and Applications 2013. 8755: 04. Bibcode:2013SPIE.8755E..04W. doi:10.1117/12.2014771. S2CID 55941907.
- "Archived copy" (PDF). Archived from the original (PDF) on September 3, 2014. Retrieved August 28, 2014.
{{cite web}}: CS1 maint: archived copy as title (link) - "Federal mobile apps lack standard security processes". June 26, 2013.
- http://armyalt.va.newsmemory.com/rss.php?date=20120406&edition=Army+AL%26T+Magazine&subsection=Field+Expedient&page=118alt2012april-june_fieldexpedient.pdf.0&id=art_0.xml&device
- "Home". Archived from the original on September 3, 2014. Retrieved August 28, 2014.
- http://www Archived 2006-03-26 at the Wayback Machine.
- "TRT Police Language Translator – Apps on Google Play".
- https://github.com/kasmus/Sample-Projects
- "Smartphones in Combat | the Praevius Innovation Group". Archived from the original on September 3, 2014. Retrieved August 28, 2014.
- file:///Users/andrealimbago/Downloads/DrPrabhakarStatement14May14SACDHearing.pdf
- Hurd, Joe; Tomb, Aaron; Archer, David; Daugherty, Jonathan (2012). "FUSE: Inter-Application Security for Android" (PDF). gilith.com.
- "Archived copy". Archived from the original on February 24, 2015. Retrieved December 6, 2014.
{{cite web}}: CS1 maint: archived copy as title (link)> - "Apps with GeoPackage introduced in DARPA TransApps program | OGC". Retrieved September 25, 2023.
- Some examples of individuals with experience with the TransApp program and the commercial sector include: Lee,Nacho Solis Archived 2014-08-29 at the Wayback Machine, Bowen Zhou, and Angelos Stavrous
- "Army Apps 1, Transformative Apps 0". May 24, 2010.
- "Report of the Committee on Armed Services" (PDF). gpo.gov. Retrieved September 25, 2023.
- Rosen, Joseph L.; Walsh, Jason W. (December 15, 2011). "The Nett Warrior System: A Case Study for the Acquisition of Soldier Systems". DTIC. Retrieved September 25, 2023.
- "The Army's New Land Warrior Gear: Why Soldiers Don't Like It". October 2009.
- For a detailed overview of NettWarrior, see: http://www.dtic.mil/dtic/tr/fulltext/u2/a555648.pdf
- Dodaro, Gene L. (June 2011). Defense Acquisitions: Assessments of Selected Weapon Programs. DIANE. ISBN 978-1-4379-8365-4.
- "Army Eyes Samsung smartphones | Defense Tech". Archived from the original on September 4, 2014. Retrieved August 28, 2014.
- "Army Troops Slam New Combat Smartphone – Breaking Defense Breaking Defense – Defense industry news, analysis and commentary". November 23, 2011.
- AEM Program 2013 army.mil
- "Defense News".
- "WIRELESS TO THE EDGE" (PDF). Archived from the original (PDF) on September 3, 2014. Retrieved August 28, 2014.