Proxy pattern
In computer programming, the proxy pattern is a software design pattern. A proxy, in its most general form, is a class functioning as an interface to something else. The proxy could interface to anything: a network connection, a large object in memory, a file, or some other resource that is expensive or impossible to duplicate. In short, a proxy is a wrapper or agent object that is being called by the client to access the real serving object behind the scenes. Use of the proxy can simply be forwarding to the real object, or can provide additional logic. In the proxy, extra functionality can be provided, for example caching when operations on the real object are resource intensive, or checking preconditions before operations on the real object are invoked. For the client, usage of a proxy object is similar to using the real object, because both implement the same interface.
Overview
The Proxy [1] design pattern is one of the twenty-three well-known GoF design patterns that describe how to solve recurring design problems to design flexible and reusable object-oriented software, that is, objects that are easier to implement, change, test, and reuse.
What problems can the Proxy design pattern solve? [2]
- The access to an object should be controlled.
- Additional functionality should be provided when accessing an object.
When accessing sensitive objects, for example, it should be possible to check that clients have the needed access rights.
What solution does the Proxy design pattern describe?
Define a separate Proxy object that
- can be used as substitute for another object (
Subject) and - implements additional functionality to control the access to this subject.
This makes it possible to work through a Proxy object to perform additional functionality when accessing a subject. For example, to check the access rights of clients accessing a sensitive object.
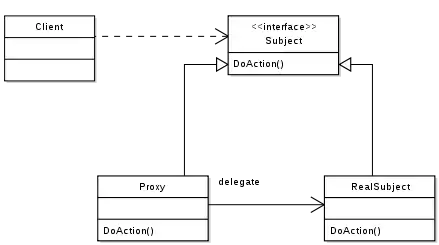
To act as substitute for a subject, a proxy must implement the Subject interface.
Clients can't tell whether they work with a subject or its proxy.
See also the UML class and sequence diagram below.
Structure
UML class and sequence diagram
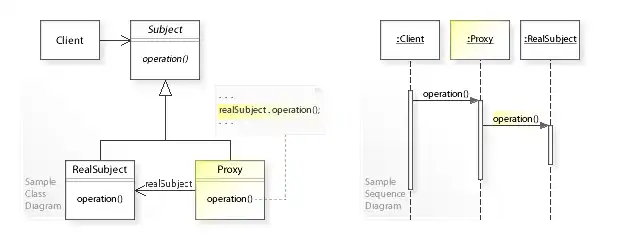
In the above UML class diagram,
the Proxy class implements the Subject interface so that it can act as substitute for Subject objects. It maintains a reference (realSubject)
to the substituted object (RealSubject) so that it can forward requests to it
(realSubject.operation()).
The sequence diagram
shows the run-time interactions: The Client object
works through a Proxy object that
controls the access to a RealSubject object.
In this example, the Proxy forwards the request to the RealSubject, which performs the request.
Possible usage scenarios
Remote proxy
In distributed object communication, a local object represents a remote object (one that belongs to a different address space). The local object is a proxy for the remote object, and method invocation on the local object results in remote method invocation on the remote object. An example would be an ATM implementation, where the ATM might hold proxy objects for bank information that exists in the remote server.
Virtual proxy
In place of a complex or heavy object, a skeleton representation may be advantageous in some cases. When an underlying image is huge in size, it may be represented using a virtual proxy object, loading the real object on demand.
Protection proxy
A protection proxy might be used to control access to a resource based on access rights.
References
- Erich Gamma, Richard Helm, Ralph Johnson, John Vlissides (1994). Design Patterns: Elements of Reusable Object-Oriented Software. Addison Wesley. pp. 207ff. ISBN 0-201-63361-2.
{{cite book}}: CS1 maint: multiple names: authors list (link) - "The Proxy design pattern - Problem, Solution, and Applicability". w3sDesign.com. Retrieved 2017-08-12.
- "The Proxy design pattern - Structure and Collaboration". w3sDesign.com. Retrieved 2017-08-12.
External links
- Geary, David (February 22, 2002). "Take control with the Proxy design pattern". JavaWorld. Retrieved 2020-07-20.
- PerfectJPattern Open Source Project, Provides componentized implementation of the Proxy Pattern in Java
- Adapter vs. Proxy vs. Facade Pattern Comparison at the Wayback Machine (archived 2012-03-11)
- Proxy Design Pattern
- Proxy pattern C++ implementation example at the Wayback Machine (archived 2014-10-19)
- Proxy pattern description from the Portland Pattern Repository