This article was co-authored by wikiHow Staff. Our trained team of editors and researchers validate articles for accuracy and comprehensiveness. wikiHow's Content Management Team carefully monitors the work from our editorial staff to ensure that each article is backed by trusted research and meets our high quality standards.
There are 7 references cited in this article, which can be found at the bottom of the page.
The wikiHow Video Team also followed the article's instructions and verified that they work.
This article has been viewed 357,711 times.
Learn more...
Secret notes can be a fun way to communicate with others in-the-know. There are many kinds of ciphers and methods for creating virtually unbreakable messages. Whether you’re sending a love note or a top secret, a secret note will keep your message safe.
Steps
Sample Notes
Making a Substitution Cipher
-
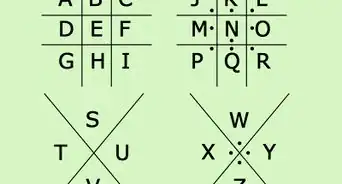
1Substitute letters for other letters. In a simple substitution cipher, you can assigning letter values to other letters. For example, A may equal C and and F might equal J. Make sure you don’t choose easy combinations like A = B or A = Z. They’ll be easily broken.[1]
- Make decoder rings. Those decoder rings you got in a box of cereal years ago may come in handy, but you can make your own too if you want. Write your letters, A through Z, in a large circle. Then, write the substituted letters inside the large circle to form their own smaller circle. Now you’ll have a key for your cipher.
- Randomize the cipher. Once you’ve got your keys and your friends have theirs too, you can cut out both rings from the paper. Turn the smaller ring inside the larger outer ring to create new substitutions. When you pass your note, write what A equals, and the reader will know where to set their rings.
-
2Substitute your own symbols for letters. To make a slightly more complicated substitution cipher, you can make your own simple symbols to stand in for letters. The more each symbol looks different than the letter it represents, the harder the code will be to crack. Make sure each symbol is also simple and easy to draw quickly.[2]
- Create a key for your new language. Make a master key that shows which letter matches up with each symbol. As you practice writing in your new script, you’ll become more familiar with the symbols, but you’ll need a key at first to remember which is which.
- Share the key with friends. Your language won’t be of much use if only you can read the notes you pass! Share the key with your friends, advising them to keep it safe so that no one else finds and learns the symbols.
- Write your messages in the new language. Practice the symbols until you can read and write them as quickly as your native language. It’ll take a while, but you’ll get to know the symbols well over time.
Advertisement -
3Substitute letters from another language. For example, swap A with (α) Alpha, B with (β) Beta, C with (Χ) Chi, etc. from the Greek alphabet..
- Use similar characters for missing letters. Some foreign alphabets may not contain all the letters in your language. Greek doesn't have Y, but there's a visually similar Upsilon (Y in capitals), so you might use that instead. Make sure your reader knows that you’re going to be substituting some letters for others not in the language.
- Test some examples. For example: "See you tonight" becomes "ΣΕΕ ΤΗΟΥ ΤΟΝΙΓΗΤ,” with “you” subbed out for “thou” because Greek doesn’t have a character for “Y”.
-
4Substitute equations for numbers. Numbers tend to stick out in messages with a lot of text, so try to find a better way to to hide them in your cipher. For example, replace the "8" in "See you tonight, 8 o'clock" with "√(128/2)". The 8 is replaced by a simple math: the square root of (128/2=64)=8.
-
5Be aware that substitution ciphers can be broken. It’s relatively easy to crack a substitution code, because you’re still using your native language and only swapping out the letters for other letters or symbols. Words like “and”, “you” and “the”, which will show up frequently in your messages, and can be found out and used to piece together parts of a key. Common letters like E, T and A also help code-breakers to decipher your message.[3]
Using a Transposition Cipher
-
1Use a simple transposition cipher. Transposition codes take your normal message and rearrange the letters according to a simple, agreed upon rule. This type of cipher can be harder to crack than a substitution cipher, because there will be no frequently used words to be found: they’ll all be scrambled.[4]
- Write your message normally. Because you’re going to be scrambling the message, you’ll need the normal message as a starting place. Choose something simple to start with like, “How are you today”
- Decide how to rearrange the letters. A simple transposition cipher, for example, might take each letter and place them in reverse order within the word, but not the sentence. “How are you today” would become “woh era uoy yadot”.
- Let your friends know the rearranging order. They’ll need to know how you scrambled the words so that they can read your messages. Pick something a little more difficult than just reversing the letters, as the example of “woh era uoy yadot” can be easily cracked.
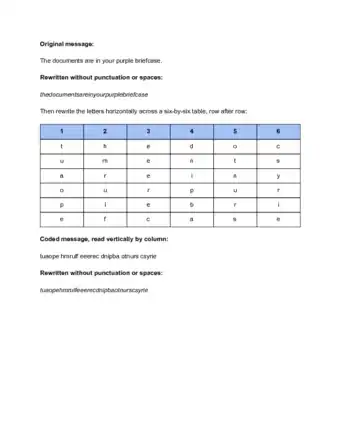
- Try using a matrix. Draw large box on a piece of paper and divide it evenly into rows and columns. Write your normal message with one letter written in each smaller box. Your new message will be made by making the vertical columns into sentences instead of the horizontal ones. To decode, your friends will have to make their own grid, write the sentences vertically, then read left to right as normal.
-
2Use the snake method. This method is a type of transposition cipher, in that the letters are written and arranged up and down a paper instead of straight across, creating a block of text. Be aware that this may be easy to crack, because none of the words are scrambled.
- Write your message starting in one of the corners of the paper. Make a column up or down from where you started. Write in a straight line all the way to the next edge of the paper.
- Write the next column when you reach the edge. Once you reach the edge of the first column, start writing the next line in the opposite direction. If you started writing upwards from the bottom left corner, you’ll now write in a line going down to the next edge of the page.
- Repeat for each column. Continue writing your message up and down the paper, like a snake. When looked at by anyone else, they’ll only see a block of text that makes no sense when read from left to right.
- Sign your message with a small snake. Your friends will know how you’ve written the message and how to read it. Meanwhile, no one else will know what it means.
Making a Cipher Based on Text
-
1Use a passage cipher. Choose a short passage, making sure that every letter in the alphabet is used to begin a word in the passage. If it’s too hard to find one with any Xs and Zs, you can write your own.
- Number each of the words. Starting with the first word in the passage, count the words and then number them left to write. It should look like: “A1 fine2 day3 to4 go5 out6 running7…”, etc.
- Write your message using the numbers. In the example, A = 1, F = 2, D = 3, 4 = T, 5 = G, 6 = O and 7 = R. To spell the word “far”, you’d write 217.
- Share the passage with your friends. Leave it un-numbered, and have them count the letters mentally. To everyone else, the key will look like a normal paragraph, and no one will know it’s the key to a code.
-
2Use a Book Cipher. Like a passage cipher, you’ll use the words in the book to make up the words of your message. You’ll make up a rule that determines how the words are found, and this will be used to transmit them message.[5]
- Pick your book. This should be a common book that both you and the receiver of the message own. It must be the exact same edition so that the words and pages are in exactly the same places.
- Determine your method. Book ciphers often use three numbers separated by commas to denote information. (100,28,5) might mean that the target word is on the 100th page, the 28th line and the 5th word in that line.
- Write your messages using the method. Your “words” will be made up of groups of numbers and almost impossible to break. Book ciphers are so difficult to crack because to break it, someone will have to know and possess the exact edition of the book you used.
Making a Hidden Message
-
1Make invisible ink with a lemon. Invisible ink can be made from lemon juice and water. The lemon juice mixture is clear when applied to paper, but turns brown when heated up due to oxidization. This makes passing secret notes easy, because no one will even know you’ve written anything on the paper.[6]
- Squeeze half of a lemon into a small bowl and mix in a few drops of water.
- Use a paintbrush to apply the lemon juice to the paper, writing as you normally would. Make sure not to use too much of the liquid, as it can make the paper fall soggy and it could fall apart.
- To decode, heat the paper with a hair dryer, or hold it under a warm light bulb. The clear lemon juice will slowly turn brown as it warms up.
-
2Make corn-starch invisible ink. This invisible ink takes a few more obscure ingredients than lemon juice alone, but if you have corn starch and iodine, it works just as well. You'll need access to a stove too.[7]
- Mix two tablespoons of corn starch and four tablespoons of water in a small pot.
- Heat the mixture on medium heat until warm, but not hot: around 3 or 4 minutes.
- Dip a toothpick into the corn starch solution and use it to write your message on the paper. It will dry clear and look like a normal piece of paper.
- To make the decoding solution, mix one teaspoon of iodine with ten teaspoons of water in a bowl. Mix well.
- Dip a sponge in the iodine solution and wring it out so it's damp. Carefully wipe the sponge over the paper to decode the message: it should turn purple. Be careful not to make the paper too damp and soggy!
-
3Make a mini whiteboard. This method doesn't create a hidden message, per se, but it allows the receiver of the message to wipe it away quickly and easily. This will keep any message safe from prying eyes and essentially hidden. You'll need glossy tape, a small notecard or paper and a felt tipped pen.
- Cover a small card or paper with tape. Make sure the it’s the glossy kind of tape, like packing tape, not the matte “invisible” type of tape.
- Write your message on the tape with a felt tipped pen.
- Pass the note to your friend. It will look like an ordinary note: colored marker on regular paper.
- Your friend can now easily wipe the message in felt tipped pen off of the glossy surface, destroying the secret message as soon as it's read.
Community Q&A
-
QuestionWhat if the person does not know the trick to opening my note?
 Community AnswerTalk to them somewhere private (phone, bathroom, text, etc.) and make sure they understand before you start to pass the notes. You could do a practice run to begin with, showing them a blank note in the format you intend to use and getting them to open it or read it as prepared.
Community AnswerTalk to them somewhere private (phone, bathroom, text, etc.) and make sure they understand before you start to pass the notes. You could do a practice run to begin with, showing them a blank note in the format you intend to use and getting them to open it or read it as prepared. -
QuestionIs it okay if the teacher reads it as long he/she doesn't know the code?
 Katyayani KathyCommunity AnswerSome teachers who are very close to you and don't scold you maybe will forgive you. But you must still be careful as the teacher will still be upset as you were passing notes and you may get in trouble.
Katyayani KathyCommunity AnswerSome teachers who are very close to you and don't scold you maybe will forgive you. But you must still be careful as the teacher will still be upset as you were passing notes and you may get in trouble. -
QuestionWhat if someone gets the paper and it was not the person I wanted to give it to?
 Community AnswerIf it is in code, the person who intercepted it won't be able to read it.
Community AnswerIf it is in code, the person who intercepted it won't be able to read it.
Warnings
- Be careful passing notes in class. Even if they’re encrypted, your teacher will still be upset with you for passing notes and you may get in trouble.⧼thumbs_response⧽
- Never use your codes to write about anything illegal! Even if you think it’s perfectly secure, there are many government agents whose entire job is to find and crack codes that they find suspicious.⧼thumbs_response⧽
References
- ↑ http://www.exploratorium.edu/ronh/secret/secret.html
- ↑ https://www.youtube.com/watch?v=TvMHjjVcu1A
- ↑ http://www.simonsingh.net/The_Black_Chamber/crackingsubstitution.html
- ↑ http://crypto.interactive-maths.com/simple-transposition-ciphers.html
- ↑ http://www.cs.miami.edu/home/burt/journal/crypto/bookcipher/
- ↑ http://www.sciencekids.co.nz/experiments/invisibleink.html
- ↑ http://mypages.iit.edu/~smile/ch9602.html