This article was co-authored by Stan Kats and by wikiHow staff writer, Nicole Levine, MFA. Stan Kats is a Professional Technologist and the COO and Chief Technologist for The STG IT Consulting Group in West Hollywood, California. Stan provides comprehensive technology solutions to businesses through managed IT services, and for individuals through his consumer service business, Stan's Tech Garage. Stan holds a BA in International Relations from The University of Southern California. He began his career working in the Fortune 500 IT world. Stan founded his companies to offer an enterprise-level of expertise for small businesses and individuals.
There are 11 references cited in this article, which can be found at the bottom of the page.
This article has been viewed 38,530 times.
If you live amid a stream of Wi-Fi locations, or you have many computers in one building, you may be concerned about the potential of other computers being able to access your printer and files via the internet. The only way to guarantee that no other computers will be able to access yours is to completely disconnect it from the Internet. However, you can set up your computer to defend itself while still being connected. Downloading a Firewall and Blocking sharing programs is the best way to do this.
Steps
Disabling File and Printer Sharing
-
1Stop sharing your printer with other users on the network. If you have a printer, you may unknowingly be sharing it with others. Fortunately, it's easy to disable printer sharing in your settings.
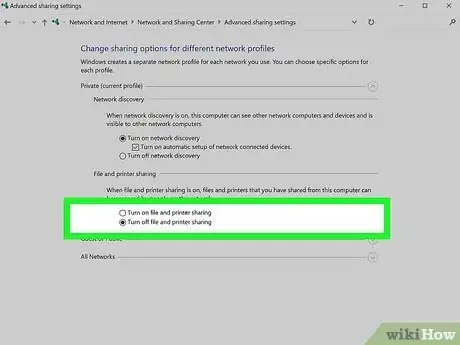
- Windows: In the Control Panel, click Network and Internet and then Network and Sharing Center. Click Change advanced sharing settings and then choose Turn off file and printer sharing.[1]
- macOS: Click the Apple menu and go to System Preferences… > Sharing. Remove the checkmark next to "Printer" to stop sharing your printer.[2]
-
2Check your network file sharing settings. If your PC or Mac is set up to share files over the network, people who are connected to the same Wi-Fi or wired network as you may be able to access certain files on your computer. To disable file sharing:
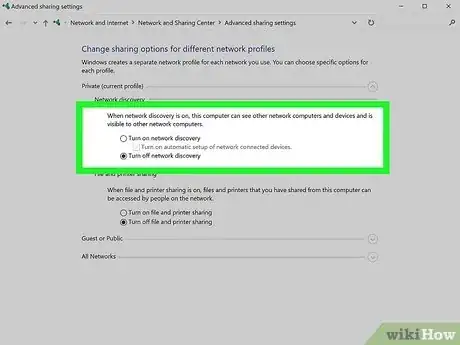
- Windows: Turning off printer sharing in the Network and Sharing Center also turns off file sharing for Windows 10 and 11. But you can go a step further and make your PC undiscoverable—in Control Panel > Network and Internet > Network and Sharing Center, click Change advanced sharing settings, and then choose Turn off network discovery.
- macOS: Click the Apple menu and go to System Preferences… > Sharing. Remove the checkmark from "File Sharing" to stop sharing all files, or check the list of users in "Users & Groups" to remove access for certain users only.[3]
Advertisement -
3Turn off Nearby Sharing in Windows. If you're using Windows 10 or 11, there's a feature on your PC that lets you share files with other users nearby. If you don't want other people to be able to send files directly to your computer while nearby, you can disable Nearby Sharing:
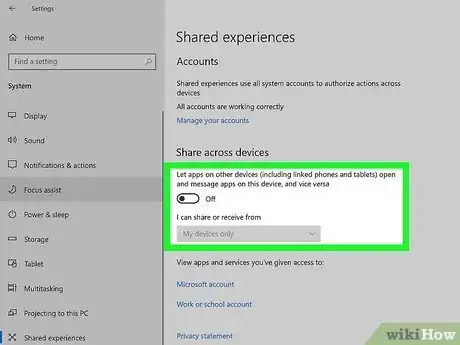
- Windows 10: In the Windows menu, go to Settings > System > Shared experiences and select Off.[4]
- Windows 11: In the Windows menu, go to Settings > System > Nearby Sharing and choose Off.
-
4Turn off AirDrop on your Mac. When AirDrop is enabled on your Mac, other people can wirelessly send documents and other files to your computer when nearby. To disable AirDrop:
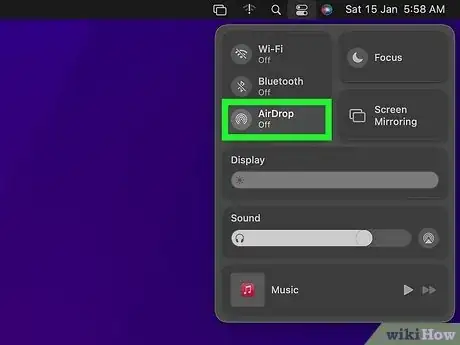
- Click the Control Center icon at the top-right corner of the screen (the two sliders).
- If the AirDrop icon is blue, click it to turn off AirDrop.[5]
Running a Malware Scan
-
1Choose your anti-malware program. There are dozens of programs you can choose from. Many are free, but if you’re willing to pay, you can get more advanced security. All of them can run a scan that detects a large majority of threats to your computer. The more advanced programs allow you to do a custom scan.[6]
- Whichever scanning program you choose, make sure it scans your registry objects. This is where you will first see problems with a hacker. Memory, startup, filesystem, and heuristic areas are also important in your scan.
-
2Install your program. Some have system pre-requisites, be sure that you use one that matches with your computer and system model. The pre-requisites will be listed before you download or install anything. If your computer doesn’t recognize the program, you’ve likely chosen one that doesn’t match the pre-requisites.
- Find your program either by inserting the disk and navigating to your computer menu or by going into your downloads and double clicking on the program.
- Select language and read through the agreement. You must accept the terms to move forward.
- Select an installation directory. Clicking next after you accept the terms will automatically select your default locations for your installation directory.
- You’re ready to install. You will be asked if you’d like to create a desktop icon and then you’ll see a final confirmation asking if you’re ready to install. Once you confirm, your installation will be completed in the next couple minutes.
-
3Run a threat scan. Open your anti-malware program. The home screen will have an option across the top that says “Scan.” Click this. Up to three scan options will pop up. Choose the first level, Threat Scan, for the most comprehensive scan. It scans all of the places that malware is known to hide.[7]
-
4Scan now. When you choose which scan you wish to run, a screen will pop up with all of your programs listed in a menu. Beneath this menu, there will be a button that says Scan Now. Click this button. This scan can take a good about of time to perform. You can watch your scan progress by keeping the program open.
- You can pause the scan at any time by clicking the button at the bottom of your progress screen.
-
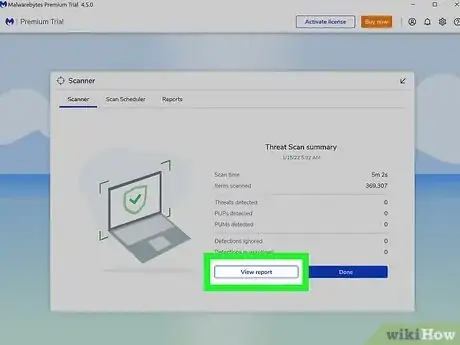
5Examine your scan results. If your computer has not been hacked, has no malware, and no other threats, your scan will display no detected threats. If there are threats, it will list them and you decide where to go from there.[8]
- Most anti-malware programs will list the threats by severity. Red will represent malware, whereas yellow often represents items that are potential danger. Remove malware to protect your computer. It is up to you which programs to keep.
- Select the boxes that you wish to remove. The programs listed will be next to a box. Check them and then click “Remove Selected.”
- Once the removal is done, you’re scan will tell you that it was quarantined.
-
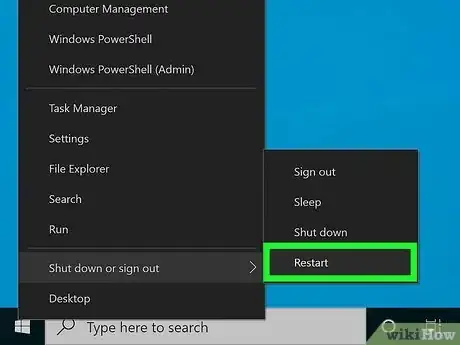
6Restart your computer. To ensure that the threat removal process is complete, you need to restart your computer. If you choose to wait, you will be reminded regularly that you need to restart it.
Using a Firewall
-
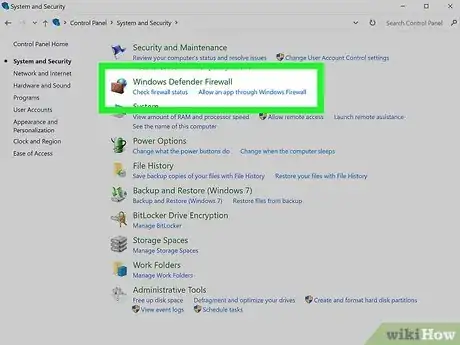
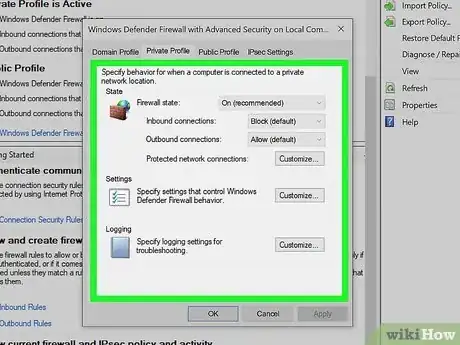
1Use Windows firewall. A firewall is a network security system that monitors and controls incoming and outgoing network traffic. This helps screen out hackers, viruses, and worms that are trying to reach your computer over the Internet.[9] Windows has built firewall protection into the program since 2001.[10] It was built to specifically protect your system from outside attacks.
-
2Add a third-party firewall. Because your built-in firewall only protects from outside attacks, you’ll want to download a third-party firewall.[11] This will help protect your computer from local programs that are abusing your network connection. There are many no-cost firewalls that will work on multiple PCs: Kerio Personal Firewall 2, Outpost Firewall Free, Sygate Personal Firewall 5.1, and Zone Labs’ ZoneAlarm 3.7 are four solid free firewalls.
- These can be found online simply by searching their names. The free download option is on the homepage for each of the programs.
-
3Disallow networks to browse. Firewalls have a default setting. This setting allows other PCs on the same network to browse. However, they won’t be able to access your files and printers. You can enable this by right-clicking the firewall’s system tray icon.[12]
- Choose options, and then Network Neighborhood.
- Select the interface you use to connect in the drop-down list that appears.
- Uncheck the box next to “Allow others to share my files and printer(s)” and then click OK.
- Now your computer is safe from local and outside attacks.
Blocking Java
-
1Disable Java. This is a program that was originally created to help run programs with ease from any Java-supporting platform. Instead, it has turned into an attack vector for hackers.[13] Although some programs still use Java, if you don’t absolutely need it, disable it.
-
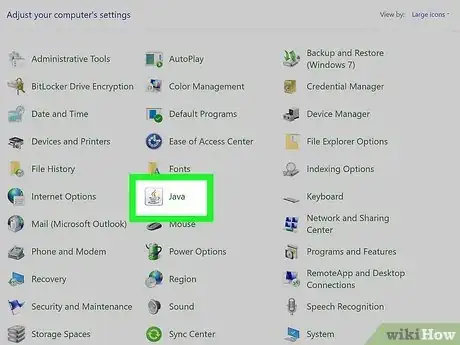
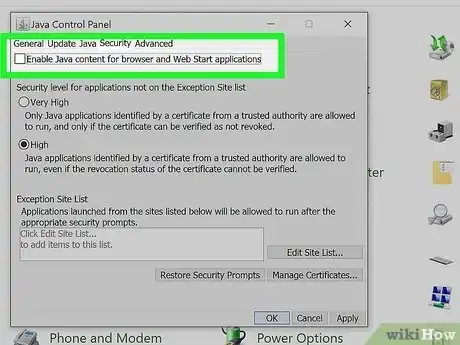
2Open your control panel. From here, launch the Java app (it looks like a steaming coffee mug). When you open the app, it will have a similar set up to your settings menu—there will be tabs across the top. Choose the tab that’s labeled “Security.”
- Find the single check box. This will be titled “Enable Java content in the browser.”
- Un-check this box. Click OK. Now you’ve disabled Java.[14]
-
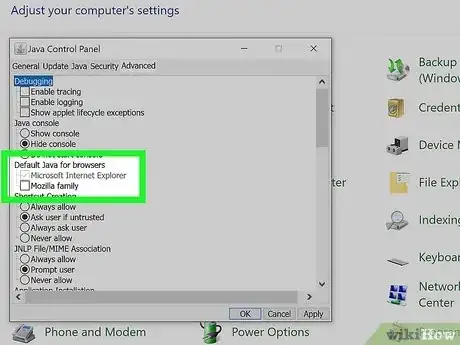
3Keep Java in one browser. If you need Java for work or to run a certain program that you can’t live without, you can enable it in a single bowser. To do this, re-launch the Java app. There will be a tab on the top that says “Advanced.” Within this tab, you’ll see and item titled “Default Java for browsers.”
- A list of your browsers will appear when you click to expand “Default Java for browsers.” The list will have boxes next to them. Check the boxes next to a browser if you wish to run Java in that browser.
Changing Your Router Settings
-
1Change the security settings. This will help protect your computer by making it more difficult for hackers to access it through your Wi-Fi. Even if you have a password set up, this will further aid the protection of your computer.
- Keep your router up-to-date so it can protect you from known vulnerabilities.[15]
-
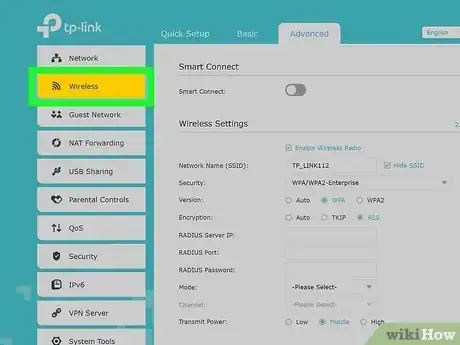
2Find the “Wireless Security” page. This will be in your wireless settings, under the tab that says “Wireless Security.” Don’t choose the tab that says “Security,” that’s for other settings. If you don’t have a password, set one up here.
- Don’t make it a weak password. It should include non-dictionary words, special characters, and numbers.
- Write this password somewhere that you’ll remember it.
-
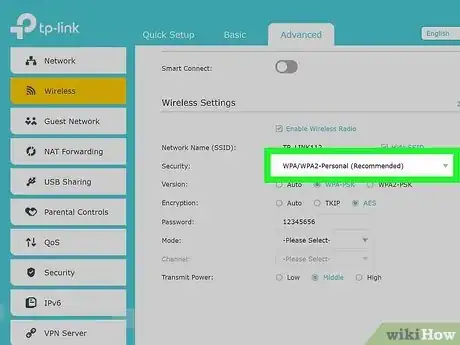
3Change your security mode. There will be a dropdown menu next to “Security Mode.” Click this and scroll to WPA2 personal. This home security system is much more difficult than the standard security system to crack. (The standard is the WEP).
Expert Q&A
-
QuestionHow can I keep other computers from accessing my computer?
 Stan KatsStan Kats is a Professional Technologist and the COO and Chief Technologist for The STG IT Consulting Group in West Hollywood, California. Stan provides comprehensive technology solutions to businesses through managed IT services, and for individuals through his consumer service business, Stan's Tech Garage. Stan holds a BA in International Relations from The University of Southern California. He began his career working in the Fortune 500 IT world. Stan founded his companies to offer an enterprise-level of expertise for small businesses and individuals.
Stan KatsStan Kats is a Professional Technologist and the COO and Chief Technologist for The STG IT Consulting Group in West Hollywood, California. Stan provides comprehensive technology solutions to businesses through managed IT services, and for individuals through his consumer service business, Stan's Tech Garage. Stan holds a BA in International Relations from The University of Southern California. He began his career working in the Fortune 500 IT world. Stan founded his companies to offer an enterprise-level of expertise for small businesses and individuals.
Professional Technologist Most firewalls out there will keep other computers from connecting to your computer. It depends on your WiFi connection, though.
Most firewalls out there will keep other computers from connecting to your computer. It depends on your WiFi connection, though. -
QuestionWill a firewall keep me safe on a public WiFi network?
 Stan KatsStan Kats is a Professional Technologist and the COO and Chief Technologist for The STG IT Consulting Group in West Hollywood, California. Stan provides comprehensive technology solutions to businesses through managed IT services, and for individuals through his consumer service business, Stan's Tech Garage. Stan holds a BA in International Relations from The University of Southern California. He began his career working in the Fortune 500 IT world. Stan founded his companies to offer an enterprise-level of expertise for small businesses and individuals.
Stan KatsStan Kats is a Professional Technologist and the COO and Chief Technologist for The STG IT Consulting Group in West Hollywood, California. Stan provides comprehensive technology solutions to businesses through managed IT services, and for individuals through his consumer service business, Stan's Tech Garage. Stan holds a BA in International Relations from The University of Southern California. He began his career working in the Fortune 500 IT world. Stan founded his companies to offer an enterprise-level of expertise for small businesses and individuals.
Professional Technologist It may put up a bit of a fight in certain situations, but public WiFi networks can be especially unsafe. I'd recommend using a VPN if you're on a public WiFi network to mask your computer.
It may put up a bit of a fight in certain situations, but public WiFi networks can be especially unsafe. I'd recommend using a VPN if you're on a public WiFi network to mask your computer. -
QuestionHow can I keep my home network safe from hackers?
 Stan KatsStan Kats is a Professional Technologist and the COO and Chief Technologist for The STG IT Consulting Group in West Hollywood, California. Stan provides comprehensive technology solutions to businesses through managed IT services, and for individuals through his consumer service business, Stan's Tech Garage. Stan holds a BA in International Relations from The University of Southern California. He began his career working in the Fortune 500 IT world. Stan founded his companies to offer an enterprise-level of expertise for small businesses and individuals.
Stan KatsStan Kats is a Professional Technologist and the COO and Chief Technologist for The STG IT Consulting Group in West Hollywood, California. Stan provides comprehensive technology solutions to businesses through managed IT services, and for individuals through his consumer service business, Stan's Tech Garage. Stan holds a BA in International Relations from The University of Southern California. He began his career working in the Fortune 500 IT world. Stan founded his companies to offer an enterprise-level of expertise for small businesses and individuals.
Professional Technologist Keeping your router up to date will protect your home network from any vulnerabilities. You also want to keep your computer's operating system up to date for similar reasons.
Keeping your router up to date will protect your home network from any vulnerabilities. You also want to keep your computer's operating system up to date for similar reasons.
Warnings
- By allowing Java to run in a single browser, your computer is still at risk.⧼thumbs_response⧽
- Keep your network secure—don't connect to unknown WiFi networks, and make sure you use a strong password for your home WiFi network.[16]⧼thumbs_response⧽
References
- ↑ https://support.microsoft.com/en-us/windows/file-sharing-over-a-network-in-windows-10-b58704b2-f53a-4b82-7bc1-80f9994725bf
- ↑ https://support.apple.com/lt-lt/guide/mac-help/mchlp2424/mac
- ↑ https://support.apple.com/en-ke/guide/mac-help/mh17131/12.0/mac/12.0
- ↑ https://support.microsoft.com/en-us/windows/share-things-with-nearby-devices-in-windows-0efbfe40-e3e2-581b-13f4-1a0e9936c2d9#WindowsVersion=Windows_10
- ↑ https://support.apple.com/en-ke/guide/mac-help/mh35868/12.0/mac/12.0
- ↑ https://www.cisa.gov/uscert/ncas/tips/ST04-005
- ↑ https://www.cisa.gov/uscert/ncas/tips/ST04-005
- ↑ https://www.cisa.gov/uscert/ncas/tips/ST04-005
- ↑ Stan Kats. Cybersecurity Expert. Expert Interview. 24 June 2021.
- ↑ https://www.pcmag.com/how-to/do-you-need-a-personal-firewall
- ↑ https://www.cisa.gov/uscert/ncas/tips/ST04-004
- ↑ https://support.microsoft.com/en-us/topic/disable-file-and-printer-sharing-for-additional-security-3713fb7e-7c34-e60a-01f4-20f34ba38154
- ↑ https://www.pcmag.com/news/how-to-disable-java
- ↑ https://www.pcmag.com/news/how-to-disable-java
- ↑ Stan Kats. Cybersecurity Expert. Expert Interview. 24 June 2021.
- ↑ Stan Kats. Cybersecurity Expert. Expert Interview. 24 June 2021.