X
wikiHow is a “wiki,” similar to Wikipedia, which means that many of our articles are co-written by multiple authors. To create this article, 14 people, some anonymous, worked to edit and improve it over time.
This article has been viewed 201,601 times.
Learn more...
Downloading software has become a stressful task. In a world where anonymity means a great deal there are those who would throw privacy to the wind and watch your every maneuver. However there are many things you can do to upload and download anonymously, this concept will be explored below.
Steps
-
1There are many ways to hide one's tracks on the information superhighway. The main way people put a face on a computer is with the computers IP address. That number can easily be turned into a real address with minimal effort. Therefore almost all anonymous services deal solely with IP addresses. IP anti-detection can be divided into one of two categories. Namely:
- Software Based:
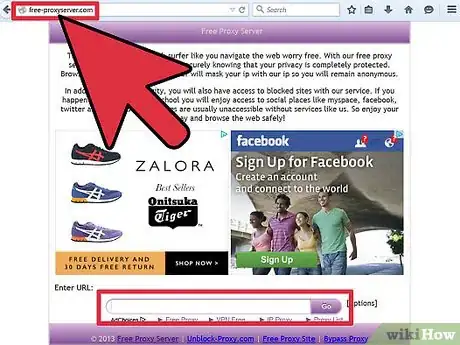
- Proxy: A proxy in simple terms is another computer out there somewhere that bounces your connection to where you want it to go. You can download add-ons for Firefox so these proxy "Addresses" can be typed in.
- List Blocking: List are compiled of various Computer addresses that people wish to block from their connection. Using this service one can, to some degree block the government, RIAA, Spyware sites and even Ads. A popular free list blocking tool is called peer guardian.
- Bounce link: Some hosting sites allow you to download a link that they themselves have in stock that users have uploaded. After a disclaimer they take no responsibility for links that users upload, some even delete IP address logs; or
- Hardware Based: By adding or removing certain parts from a computer a person can reach a level of high anonymity.
- NIC-USB: By removing your internet card you achieve perfect anonymity, they can't come through the power cord right? However, if you want to stay online it may be better to invest in some hardware that will take you there. Get yourself a high volume data recovery drive, In short a huge USB flash drive. Install an operating system and all you have to do to use a random computers BIOS setup to boot the computer up from USB. This comes in handy at pizza places with high speed, or even some coffee shops. However, you will then have to stay anonymous in real life and will eventually have to learn advanced SSH protocols.
- Differential Porting: Two computers can be hitched together using parallel or serial cables as well, given that proper hardware and software conditions are met. Using this method several computers can be hitched together with mixed proxies and ports to confuse any would be down peeper.
- Airsnorting: With a wireless laptop one can sit outside a coffee shop. By using a nameless Linux application one can find the invisible encryption keys that flow through the air during wireless transmissions thus giving you the golden ticket to their connection. This combined with SSH protocol will put you online almost anywhere.
- SSH protocol: With a small PirateRay application that uses SSH secure tunnel to one of the PirateRay servers. A user can select either a specific server or set the settings to enable the random selection of the server whenever the application starts.
- Software Based:
-
2After that, all the data that the user receives or transmits is encrypted.Advertisement
-
3All operations involving the torrent network will take place by using an IP address of a server that is located at the other end of the world. Logging on does not happen on the same servers, so the user can be assured of his security and anonymity.
Advertisement
Warnings
- The only truly anonymous connection is the one you can put in your pocket and take with you.⧼thumbs_response⧽
- Anybody sufficiently determined, like the RIAA, could break anonymity given enough time. This holds true no matter how hard you try; your traffic still has to go through many routers and servers.⧼thumbs_response⧽
- IP addresses are never really invisible. By using proxies one can slow detection down but will never download without a trace. Also note that proxies slow down Internet speed considerably.⧼thumbs_response⧽
- The best way to avoid being caught is not to do anything illegal. Seek out legal alternatives whenever possible, even if it is not as convenient.⧼thumbs_response⧽
- Laptops have IPs just like desktops.⧼thumbs_response⧽
Advertisement
About This Article
Advertisement








-Step-23.webp)