This article was written by Jennifer Mueller, JD. Jennifer Mueller is an in-house legal expert at wikiHow. Jennifer reviews, fact-checks, and evaluates wikiHow's legal content to ensure thoroughness and accuracy. She received her JD from Indiana University Maurer School of Law in 2006.
There are 9 references cited in this article, which can be found at the bottom of the page.
This article has been viewed 96,248 times.
Hackers exploit security vulnerabilities in computers and networks to steal private data, leaving you feeling helpless and overwhelmed. However, you can report hackers and regain control. If you believe an online account has been hacked, take a deep breath and notify the provider of that account as soon as possible. They will work to get you back online. If your computer is compromised, get law enforcement involved. In the meantime, do everything you can to secure your system from further attacks.[1]
Steps
Notifying a Service Provider
-
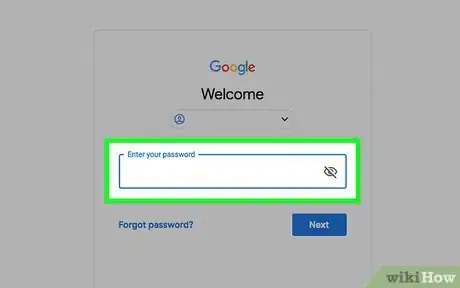
1Check your password if you can't log in. Not being able to log in is typically one of the first signs that your account has been hacked. Double-check your password to make sure you've entered it correctly or try logging in on another device to make sure you've truly lost access.[2]
- If your computer or an online account has been hacked, the hacker may change the password to something they know. If that happens, your regular password won't work.
- Most online accounts will send you an email when your password has been changed. However, if the hacker changed the email associated with the account to an email they control, you wouldn't get the email notification.
-
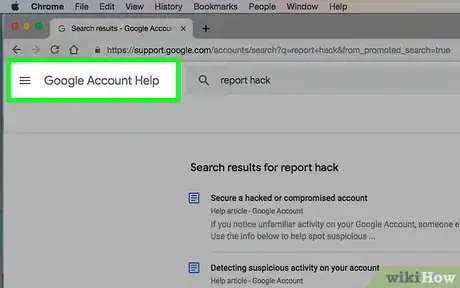
2Contact the platform directly to report the hack. Do a quick internet search for "report hack" with the name of the company that provides your online account. Typically you'll find information about how to report the incident. Each company has its own procedure for dealing with hackers and restoring access for legitimate users.[3]
- You typically have to verify your identity. This may involve providing answers to a series of security questions, scanning a valid ID, or taking a selfie while holding a card with a specific word or phrase on it.
Advertisement -
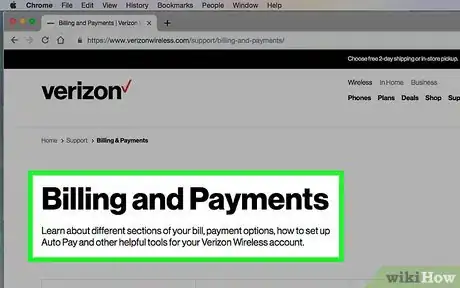
3Review your phone or internet bill for signs of overuse. If you get a bill for data that is significantly higher than usual, a hacker may have accessed your wireless network. The increased traffic can drive up your bill. Contact your phone company or internet service provider and let them know the situation.[4]
- You can typically call the regular customer service number. When the customer service agent looks at your billing pattern, it should be obvious that something's not right.
- For example, if you normally pay $50 a month for data, and then you get a bill for $900, you likely won't be liable for that expense. The company will investigate the situation and figure out what happened.
Tip: Look at usage as well. Frequent calls to international numbers, or repeated calls lasting only a few seconds, may also be signs of hacking.
-
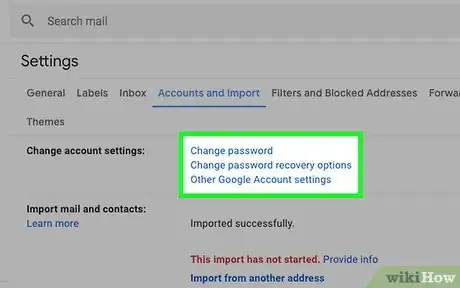
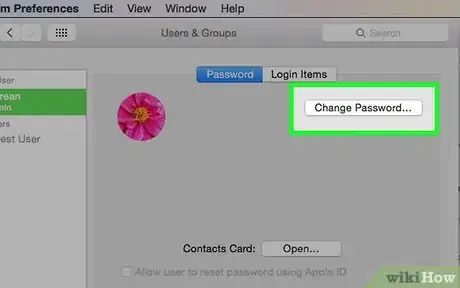
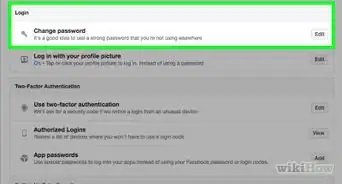
4Change your passwords when you regain access. After your account has been restored, create a new password that is complex and difficult for anyone else to guess. Check any accounts that are linked to the hacked account and make sure they're still secure.[5]
- For example, if you had a method of payment saved on the hacked account, the hackers may have been able to access that credit card or bank account. Notify your bank or credit card company, if necessary, and ask to have a fraud alert put on your account.
- If you've used the same password for other online accounts, change the password on those as well. Make sure every password you use is unique.
- Turn on 2-factor identification, if the option is available. In addition to entering a password, you will have to enter a code sent to you through text or email before you can access your account. This adds an extra layer of security for you.
Alerting Law Enforcement
-
1Recognize signs that you've been hacked. Hackers may install spyware or malware that bogs down your system, causing your computer to process more slowly or overheat. If your computer isn't as fast as it normally is, overheats frequently, or crashes, it may be a sign that you've been hacked. [6]
- You may also have frequent pop-ups on your computer or unfamiliar icons on your desktop or start menu.
- Hackers may also delete or move files. If your computer won't open a file because it's corrupted, that may be another sign that you've been hacked.
Tip: Where possible, eliminate other potential causes of computer malfunction before you jump to the conclusion that you've been hacked. You may want to take it in for a professional evaluation.
-
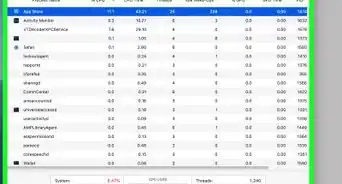
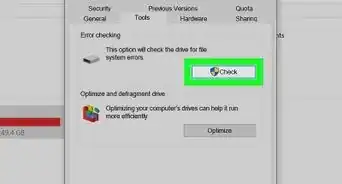
2Run a virus scan on your computer. Your antivirus software should be able to detect any spyware or malware running on your computer, and either delete or quarantine it. After the scan, read the scan report to confirm the files were deleted.[7]
- If you find a suspicious file on your computer, don't try to delete it on your own. It likely has built-in protections to keep it from being deleted, and attempting to remove it may make the problem worse.
-
3Determine which law enforcement agency to contact. In most countries, hacking laws are enforced at the national level. There may be a specific agency or task force that you need to contact to report the hackers. Check that agency's website to find out how to file a report and what information must be included in the report.[8]
- For example, in the US you would contact the FBI or the US Secret Service.
- You typically can find the right agency through a simple online search for "report hacking" with the name of your country. If you can't find the agency this way, call the non-emergency number for your local law enforcement agency and ask them who you should contact.
-
4Gather information about the intrusion. Cybercrime websites typically include a list of information you should include when you report hackers to law enforcement. Generally, try to find as much evidence as you can. Even the smallest detail may help investigators identify the hackers at fault.[9]
- If you ran a virus scan on your computer, the information in the scan report may be of interest to law enforcement. Take note of any file names or other information that might lead investigators to the hackers.
- If you have any theories as to how the hackers accessed your system, provide those to law enforcement as well. For example, spyware or malware may have come from an email attachment you downloaded.
- Write down approximate dates and times that you noticed problems with your computer or other evidence of hacking. If you were contacted by the hackers, keep the complete email – there may be information in the header that can help identify or locate the hackers.
-
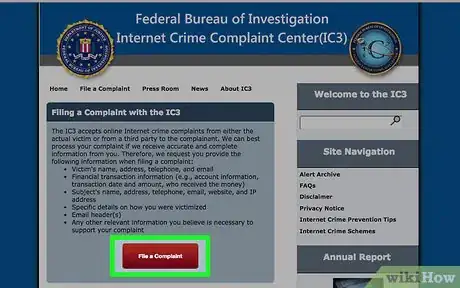
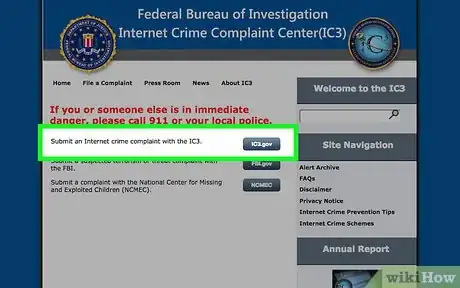
5Submit your report to the appropriate law enforcement agency. You typically have the option of reporting hackers online. If you file an online report, you usually need a working email address so the agency can confirm receipt of your report and update you on its status.[10]
- For example, if you live in the US you can report hackers to the FBI using the Internet Crime Complaint Center at https://www.ic3.gov/default.aspx. You also have the option of going in person to a local FBI office.
- You may have the option of filing your report anonymously. However, it's usually better to identify yourself and provide contact information. That way investigators can get in touch with you if they have questions or need additional information from you.
-
6File a report with local law enforcement if you feel threatened. Hackers typically are after private data or financial information and have no interest in harming you personally. However, if you've been physically threatened or if you feel your safety is at risk, call the local police.
- You might also want to file a report with the local police if you know the person who hacked you or if you know they live nearby.
- It's generally better to go to the local police precinct in person or call the non-emergency line. Even serious online threats seldom rise to the level of an emergency.
-
7Follow up on your report if necessary. Typically, the law enforcement agency won't update you on the status of any investigation. However, if you find additional information or evidence related to the hacking, contact the agency and let them know.[11]
- If the agency is able to identify and apprehend the hackers, you may receive a call from a prosecutor with questions about your report or any evidence you submitted.
Tip: Use caution if you're contacted by someone who claims to be from law enforcement. Verify their ID and call them back yourself if possible. This is a tactic hackers use to exploit people if they have reason to believe they've been reported.
Preventing Hacking
-
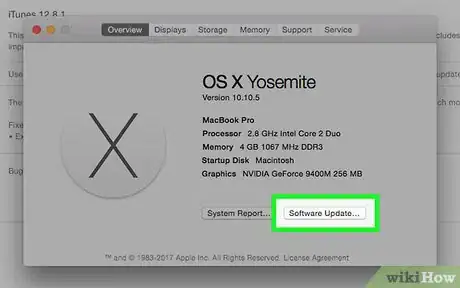
1Install the most recent operating system. Computer manufacturers regularly update their operating systems to address security vulnerabilities. Older operating systems that haven't been updated in awhile typically are less secure.[12]
- Many operating systems are available for free. Make sure you're downloading from the manufacturer directly, or from another reliable source. Check for a lock icon in the address bar to verify that the website is secure before you download.
-
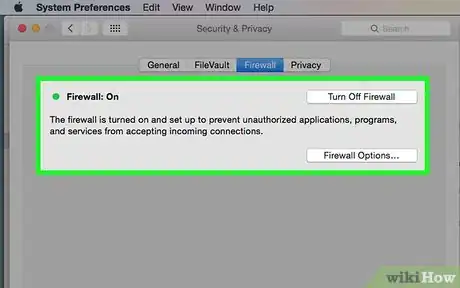
2Use up-to-date antivirus protection on your computer. Many new computers come with antivirus and firewall programs preinstalled. All you have to do is activate them and make sure they're updated regularly. The easiest way to do this is to turn on automatic updates.[13]
- Run a virus scan at least once a week, or set up your antivirus program to do this automatically.
-
3Choose complex passwords and change them regularly. The passwords you use to access your computer or online accounts should each be unique, complex, and difficult for anyone else to guess. Avoid using simple words or phrases, or identifying information such as your birthday.[14]
- Change your passwords at least twice a year. You may want to change the passwords for financial accounts more often.
Tip: Most computers have a password manager that you can use to create and store online passwords. If you use a password manager, make sure it's encrypted and that you have a strong password locking your computer.
-
4Delete emails or social media messages that seem suspicious. Hackers often send emails to attempt to trick you into giving them access to your computer or your online accounts. If you get an email or social media message from a stranger or a sender you can't verify, delete it immediately rather than responding.[15]
- For example, if you get a social media message from a friend asking you for money, contact the friend directly and ask them about the message. It could be someone who has hacked their account and is now attempting to extort money from you.
-
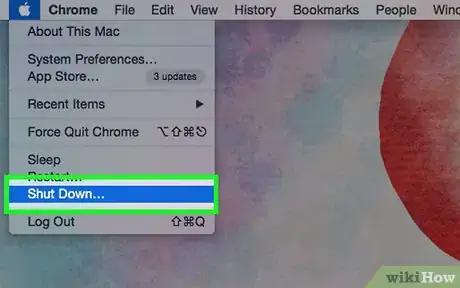
5Turn your computer off when you're not using it. Your computer is more vulnerable to hackers if it's turned on all the time. Hackers trying to access a network or system will look for a computer that's not being used so they won't be interrupted.[16]
- Keep your computers and electronic devices turned off at night unless you're using them. You may also want to turn off your wireless network when you're not using it, such as when you're not at home or at night when you're sleeping.
-
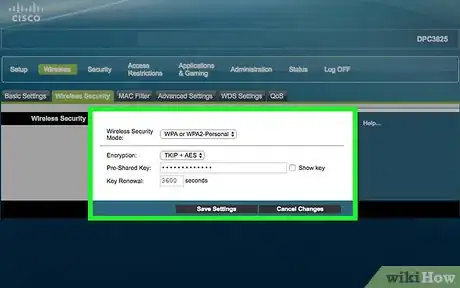
6Secure and encrypt your home WiFi network. If you have a WiFi network at home, set up a password to access it and use the highest level of encryption provided by your network router. If your network is open, hackers can use it to access your computer, as well as run up your data usage.[17]
- Most newer routers have intuitive interfaces or mobile phone apps that allow you to easily monitor your network and update security settings.
References
- ↑ https://www.acorn.gov.au/learn-about-cybercrime/attacks-computer-systems
- ↑ https://www.acorn.gov.au/learn-about-cybercrime/attacks-computer-systems
- ↑ https://www.popsci.com/what-to-do-after-hack#page-2
- ↑ https://www.scamwatch.gov.au/types-of-scams/attempts-to-gain-your-personal-information/hacking
- ↑ https://www.popsci.com/what-to-do-after-hack#page-3
- ↑ https://www.acorn.gov.au/learn-about-cybercrime/attacks-computer-systems
- ↑ https://www.scamwatch.gov.au/types-of-scams/attempts-to-gain-your-personal-information/hacking
- ↑ https://www.justice.gov/criminal-ccips/reporting-computer-internet-related-or-intellectual-property-crime
- ↑ https://www.acorn.gov.au/learn-about-cybercrime/attacks-computer-systems
- ↑ https://www.ic3.gov/default.aspx
- ↑ https://www.acorn.gov.au/
- ↑ https://www.acorn.gov.au/protect-and-prevent/computer
- ↑ https://www.scamwatch.gov.au/types-of-scams/attempts-to-gain-your-personal-information/hacking
- ↑ https://www.scamwatch.gov.au/types-of-scams/attempts-to-gain-your-personal-information/hacking
- ↑ https://www.scamwatch.gov.au/types-of-scams/attempts-to-gain-your-personal-information/hacking
- ↑ https://www.usa.gov/online-safety
- ↑ https://www.acorn.gov.au/protect-and-prevent/computer